Apache setup SSL certificate is crucial for securing your website’s communication. This guide dives deep into the process, from understanding SSL certificates and their different types to configuring Apache to use them. We’ll cover everything from obtaining a certificate to troubleshooting common issues, ensuring your website is protected and trustworthy.
We’ll explore the technical aspects of SSL certificates, the installation process on a Linux system, and how to configure Apache for secure connections. We’ll also discuss the importance of choosing the right certificate type and managing security concerns.
Introduction to SSL Certificates
Secure Sockets Layer (SSL) certificates are essential for securing web communication. They act as digital passports, verifying the identity of a website and encrypting the data exchanged between the website and the user’s browser. This ensures that sensitive information, such as passwords and credit card details, is protected from eavesdropping and tampering. This crucial layer of security builds trust between online businesses and their customers.SSL certificates work by establishing an encrypted connection between a web server and a client’s web browser.
This process involves a series of steps, including authentication and key exchange. The certificate contains the website’s public key, which is used to encrypt data sent from the browser. The server’s private key, kept secret, is used to decrypt the data. This ensures only the intended recipient can read the information.
Different Types of SSL Certificates
Various types of SSL certificates cater to different needs and levels of verification. These variations directly impact the level of trust and the verification process required.
- Domain Validation (DV) certificates: These certificates provide the most basic level of verification. They only confirm that the applicant controls the domain name. This is relatively quick and inexpensive, making it suitable for personal websites or blogs.
- Organization Validation (OV) certificates: OV certificates go a step further, verifying the applicant’s organizational details, such as its legal existence and physical address. This enhanced verification builds more trust with visitors, demonstrating a higher level of legitimacy.
- Extended Validation (EV) certificates: EV certificates provide the highest level of verification. They thoroughly scrutinize the applicant’s organizational information, often including extensive background checks. The enhanced trust is visually represented in the browser’s address bar, with the website name displayed within a green address bar, which further boosts trust with customers.
Importance of SSL Certificates in Building Trust
SSL certificates are crucial for building trust and credibility with website visitors. They demonstrate a commitment to security, assuring visitors that their data is protected during online transactions. This leads to increased user confidence, higher conversion rates, and ultimately, a more successful online presence.
Comparison of SSL Certificate Types
| Certificate Type | Features | Use Cases |
|---|---|---|
| DV | Quick issuance, relatively inexpensive. Verifies only domain control. | Personal blogs, small businesses, websites without sensitive data. |
| OV | Verifies organizational details. Provides a stronger level of trust. | Businesses seeking a higher level of trust, e-commerce sites with moderate transaction volumes. |
| EV | Thorough verification of organizational details. Visually represented in the browser’s address bar. | Large e-commerce sites, financial institutions, and other high-value websites that handle sensitive data. |
Apache Server Setup for SSL Certificates
Setting up Apache to handle secure connections (HTTPS) is crucial for protecting sensitive data transmitted between your website and users’ browsers. This involves installing Apache, configuring it to understand SSL, and properly setting up virtual hosts. This process ensures encrypted communication and builds user trust.Configuring Apache for SSL involves several steps, from installation to virtual host configuration. Understanding these steps is vital for a secure and functioning website.
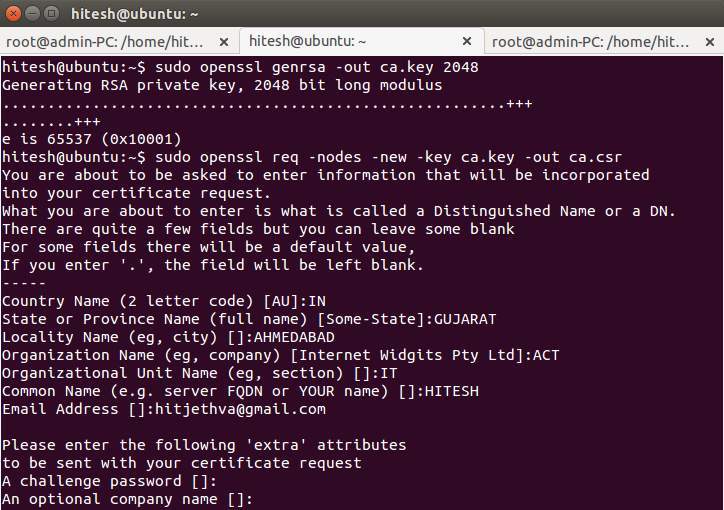
Installing Apache on Linux
The installation process for Apache varies depending on the Linux distribution. However, the general process often involves using the package manager (e.g., apt-get on Debian/Ubuntu, yum on CentOS/RHEL). Consult your distribution’s documentation for precise commands. After installation, you’ll need to verify that Apache is running correctly.
Enabling SSL Support in Apache
Enabling SSL support in Apache requires modifying the configuration files. This often involves enabling the `mod_ssl` module, which provides the necessary functionality for handling SSL connections.
Configuring the Virtual Host File for SSL
A virtual host file defines how Apache handles different websites hosted on the same server. To handle secure connections, you’ll need to modify this file to specify SSL settings. This involves adding directives for SSL certificates. This ensures that Apache knows how to respond to HTTPS requests for specific websites.
Setting up SSL certificates on Apache can be a bit tricky, but it’s crucial for secure website connections. While I’m diving deep into the technical aspects of this, it got me thinking about the unexpected connections in the digital world. For example, the surprising overlap between the gritty twang of country music and the sometimes-controversial world of cannabis is an interesting study; see the connection between country music and cannabis for more on that.
Hopefully, this exploration of secure web practices will help you navigate the digital world with confidence, just like you might navigate a dusty honky-tonk. Back to Apache, let’s get those certificates sorted!
Apache Configuration Directives for SSL
The following table Artikels essential directives for configuring SSL in Apache. These directives are crucial for setting up secure connections and ensuring the correct handling of SSL certificates.
| Directive | Description | Example |
|---|---|---|
| SSLCertificateFile | Specifies the location of the SSL certificate file. | SSLCertificateFile /etc/ssl/certs/yourdomain.crt |
| SSLCertificateKeyFile | Specifies the location of the SSL private key file. | SSLCertificateKeyFile /etc/ssl/private/yourdomain.key |
| SSLCertificateChainFile | Specifies the location of the intermediate certificate chain file (if needed). | SSLCertificateChainFile /etc/ssl/certs/intermediate.crt |
| ServerName | Specifies the hostname for which this virtual host is configured. | ServerName www.yourdomain.com |
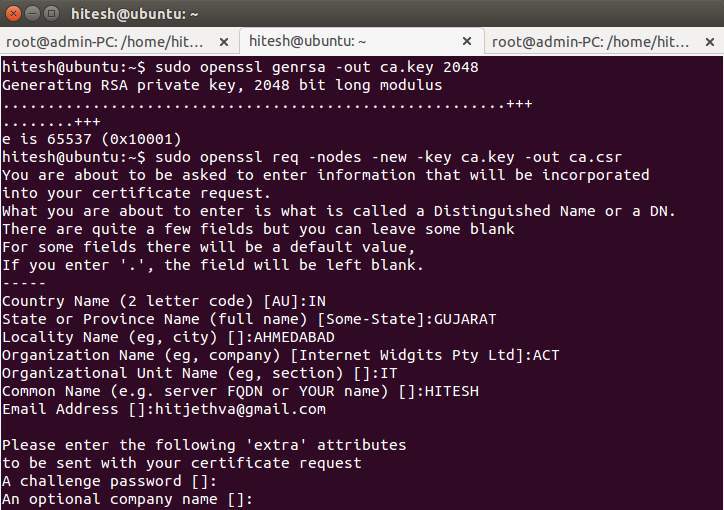
Obtaining an SSL Certificate
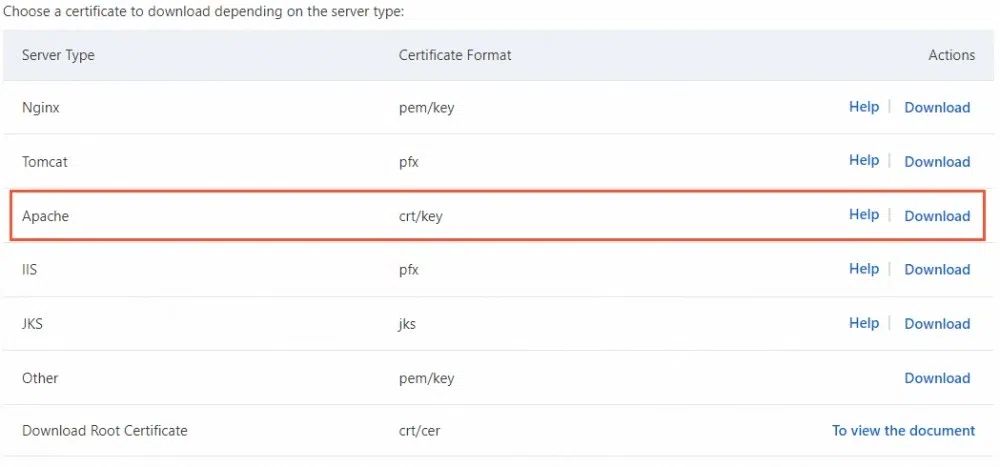
Securing your website with an SSL certificate is crucial for establishing trust with visitors and protecting sensitive data. This process involves obtaining a digital certificate from a trusted Certificate Authority (CA). This certificate verifies your website’s identity, enabling encrypted communication and preventing man-in-the-middle attacks. Understanding the different options and steps involved in obtaining and configuring an SSL certificate is vital for any website owner.
Certificate Authority (CA)
A Certificate Authority (CA) is a trusted third party that issues digital certificates. These CAs are responsible for verifying the identity of website owners and ensuring the validity of the certificates they issue. Their role is paramount in establishing trust on the internet. The verification process varies between CAs but generally involves checking the owner’s information and domain ownership.
This validation process helps ensure that only legitimate websites receive certificates.
Types of SSL Certificates
Different types of SSL certificates cater to varying needs and budgets. Free certificates are available from organizations like Let’s Encrypt, offering a viable option for basic security needs. Paid certificates, often from commercial CAs, provide enhanced features like extended validation (EV) which displays the organization’s name in the address bar, increasing trust and brand recognition.
Requesting an SSL Certificate
The process of obtaining an SSL certificate usually involves a request from the website owner. This request typically includes information about the domain name and the server details. The CA validates this information, verifying the owner’s control over the domain. The validation process can differ based on the certificate type.
Installing and Configuring an SSL Certificate
After the CA issues the certificate, it needs to be installed on the web server, typically Apache. This involves copying the certificate files to the appropriate directories and configuring the web server to use them. The process may vary based on the web server’s configuration. Crucially, the private key associated with the certificate must be securely stored and protected.
Let’s Encrypt Certificate Installation (Apache)
Let’s Encrypt is a free, automated certificate authority. Installing a Let’s Encrypt certificate on an Apache server is a straightforward process that often involves using tools like Certbot. The steps typically involve:
- Installing Certbot:
- Running Certbot to obtain the certificate:
- Configuring Apache to use the certificate:
- Verifying the installation:
The Certbot utility is a command-line tool that simplifies the process of obtaining and installing Let’s Encrypt certificates.
This command interacts with Let’s Encrypt’s servers to acquire the certificate and private key, typically using a method like the HTTP challenge.
Certbot often generates configuration changes to the Apache configuration files. It’s vital to understand these changes and ensure they’re applied correctly.
The final step is to verify that the certificate is installed correctly. This can be done by accessing the website using a web browser. A padlock icon in the address bar and a secure connection (HTTPS) indicates successful installation.
Certificate Validation and Verification
Validating and verifying an SSL certificate is essential to ensure its authenticity and prevent fraudulent certificates. Web browsers and clients employ various methods to validate certificates, checking their validity against trusted CAs. This verification process helps prevent users from connecting to potentially malicious websites. Incorrect configuration or expired certificates can result in warnings or connection errors.
Configuring Apache with the SSL Certificate
Configuring Apache to securely handle HTTPS traffic using your newly acquired SSL certificate is a crucial step. This involves correctly integrating the certificate and private key into Apache’s configuration files, ensuring secure communication channels between clients and your web server. Proper setup prevents eavesdropping and maintains the integrity of data exchanged over the network.
Configuring the SSL Virtual Host
The SSL configuration is typically handled within a virtual host block, which defines how Apache serves different domains or IP addresses. This method allows for independent configurations for each domain or service.
The virtual host configuration allows you to specify which SSL certificate to use for a particular domain or IP address. This is crucial for handling multiple domains on a single server.
Figuring out Apache setup for SSL certificates can be a bit of a headache, but it’s totally worth it for a secure website. After you get the hang of it, you’ll be ready to enjoy a delicious meal like, say, treat yourself to a comforting bowl of pork ragu. Just remember to double-check your configurations to avoid any errors and ensure everything is working smoothly.
It’s a great feeling to have your website all set up with secure SSL certificates, so keep practicing!
- Specify the SSL Certificate and Key: Within the virtual host block, identify the location of your SSL certificate and private key files. These files contain the cryptographic information necessary for secure communication. This is a fundamental step in enabling HTTPS.
- Define the Server Name: Indicate the domain name or IP address that this virtual host will serve. This association ensures that the correct certificate is used when clients connect to that specific domain or IP.
- Enable SSL/TLS Protocol: Explicitly enable the SSL/TLS protocol within the configuration. This is a critical setting to ensure the server supports secure communication protocols.
- Specify the Port: Define the port number that Apache will use for HTTPS traffic. The standard port is 443, but you can configure a custom port if needed.
SSL Configuration File Structure
The structure of your Apache SSL configuration file follows a specific format. It’s essential to understand this format to correctly configure your server.
Understanding the structure of your configuration file is vital for efficient and correct setup. Properly structured configuration ensures that your server responds appropriately to client requests.
<VirtualHost -:443> ServerName example.com SSLCertificateFile /path/to/your/certificate.crt SSLCertificateKeyFile /path/to/your/privatekey.key </VirtualHost>
This example snippet illustrates a basic virtual host configuration for HTTPS. The ServerName directive specifies the domain, and SSLCertificateFile and SSLCertificateKeyFile point to the certificate and key, respectively. The *:443 part means that this virtual host listens for HTTPS connections on all IP addresses.
Handling Different Ports for SSL and Non-SSL Traffic
It’s common practice to use different ports for secure (HTTPS) and non-secure (HTTP) traffic. This separation enhances security and simplifies management.
- Non-SSL Port (HTTP): Configure a virtual host for standard HTTP traffic on port 80.
- SSL Port (HTTPS): Configure a separate virtual host for HTTPS traffic on port 443. This is a standard setup for maintaining security and facilitating client requests.
HTTPS Request Flow Diagram
The following diagram illustrates the flow of an HTTPS request from a client to an Apache server equipped with an SSL certificate.
(Imagine a simple diagram here showing a client, an Apache server with SSL certificate, and the steps of the handshake and data transfer. It should illustrate the client requesting HTTPS, the SSL handshake process, and secure transmission of data. It should clearly show the client initiating the connection, the exchange of cryptographic keys, and the encrypted data transfer.)
Troubleshooting SSL Certificate Issues: Apache Setup Ssl Certificate
Setting up SSL certificates for your Apache web server can be tricky, and errors are common. This section will delve into the most frequent issues encountered during SSL certificate configuration and provide practical solutions for resolving them. Understanding these problems and their solutions is crucial for maintaining a secure and functioning website.
Common SSL Certificate Errors
Troubleshooting SSL certificate errors often involves a systematic approach. Carefully examining server logs and scrutinizing the certificate details are fundamental steps in identifying the root cause. Errors like “ERR_SSL_PROTOCOL_ERROR” or “ERR_CERT_AUTHORITY_INVALID” signal specific problems that need targeted solutions.
Identifying and Resolving Errors
The first step in resolving any SSL certificate error is to identify its specific nature. Comprehensive server logs provide valuable insights into the error messages. These logs typically contain details about the error type, timestamp, and relevant server actions. By meticulously reviewing these logs, you can pinpoint the precise error and understand its origin.
Checking Certificate Validity
Validating the certificate’s validity is essential to confirm that the certificate is correctly installed and trusted by the browser. Tools like OpenSSL can be used to verify the certificate’s validity and the chain of trust. Using OpenSSL commands, you can examine the certificate’s details, expiration date, and the certificate authority (CA) that issued it.
Verifying the Server Configuration
Ensuring the Apache configuration is correct is critical. Misconfigurations can lead to various SSL errors. Reviewing the Apache virtual host configuration file (e.g., `httpd.conf` or `apache2.conf`) is crucial. Ensure that the SSL directives are correctly configured, the certificate and key files are correctly specified, and the appropriate virtual host is defined. Double-check that the correct paths to the certificate and key files are specified within the configuration file.
Setting up an SSL certificate on Apache is crucial for secure website connections. However, the political landscape is also shifting, with the fate of Trump’s cabinet picks uncertain as Republicans prepare to take power in the Senate, potentially impacting future policy decisions that could indirectly affect online security protocols. Fortunately, there are straightforward steps to secure your website’s connection, ensuring users have a smooth experience regardless of the political climate.
Checking the Certificate Chain
A critical aspect of SSL certificate validation is the certificate chain. The chain links the certificate issued by the CA to the root CA certificates trusted by the browser. A broken chain can lead to errors like “ERR_CERT_AUTHORITY_INVALID.” Using OpenSSL tools, you can examine the certificate chain to identify any missing or invalid certificates in the chain.
Troubleshooting Table
The table below summarizes common SSL certificate errors and their potential solutions. Properly identifying the error and implementing the corresponding solution will help to restore SSL functionality.
| Error | Potential Solution |
|---|---|
| ERR_SSL_PROTOCOL_ERROR | Verify the Apache server’s SSL protocol version is compatible with the client. Check for mismatched SSL/TLS versions between the server and the client. Review the server’s configuration to ensure it supports the client’s protocol. |
| ERR_CERT_AUTHORITY_INVALID | Verify the certificate chain is complete and valid. Ensure the intermediate certificates are correctly installed and the root CA certificate is trusted by the browser. Check the certificate’s validity and expiration dates. |
| SSL certificate not found | Double-check the paths to the certificate and key files in the Apache configuration. Ensure the files exist and are accessible to the Apache server. |
Security Considerations
Securing your website with an SSL certificate is a crucial step towards protecting user data and building trust. However, the journey doesn’t end with installation. Robust security practices for managing SSL certificates are paramount to maintaining the integrity and reliability of your website. This section delves into critical security considerations for certificate management, including storage, handling, renewal, and the use of crucial tools like CRLs and OCSP stapling.
Certificate Storage and Handling Procedures
Proper storage and handling of your SSL certificate and private key are essential to prevent unauthorized access. Compromised private keys can lead to severe security breaches, allowing attackers to impersonate your website and potentially steal sensitive information. Following established procedures for managing these sensitive assets is vital.
- Secure Storage of Private Keys: Never store private keys in easily accessible locations. Use strong password protection, preferably employing a dedicated key management system. Never commit private keys to version control systems, such as Git. The private key should be protected with a strong passphrase, and the passphrase should be stored separately from the private key itself. It is recommended to utilize a hardware security module (HSM) to store and manage your private key if possible.
- Access Control: Implement strict access controls to limit who can access the certificate and private key. Only authorized personnel should have the necessary permissions. Employ robust authentication mechanisms and authorization protocols to control access and monitor all activities related to the SSL certificate and private key.
Maintaining Certificate and Private Key Integrity
Protecting the integrity of your SSL certificate and private key is paramount. Corruption or modification of these assets can compromise the security of your website.
- Regular Audits: Conduct regular audits of your certificate and private key management procedures. Assess potential vulnerabilities and ensure that your procedures align with current best practices. Regular security audits will help identify any weaknesses or vulnerabilities in your system. This includes reviewing access logs, checking for unauthorized access attempts, and analyzing security incidents.
- Strong Passphrases: Use strong, unique, and complex passphrases to protect your private key. Do not reuse passwords across different accounts, and change them regularly. Use a password manager to help manage your passwords securely.
Regular Certificate Renewal
Regular certificate renewal is essential for maintaining continuous website security. Expired certificates expose your website to vulnerabilities and can damage your site’s reputation. Planning ahead and setting up automated renewal processes is crucial.
- Automated Renewal Systems: Implement automated certificate renewal systems to ensure timely renewals. This will prevent your website from becoming vulnerable due to an expired certificate. Using a system that monitors and automatically renews your certificates at least 30 days before expiration is highly recommended.
- Renewal Scheduling: Establish a schedule for checking certificate expiry dates and proactively initiate the renewal process well in advance. Using a system to track the expiry date and proactively initiate the renewal process is an important security practice.
Certificate Revocation Lists (CRLs) and OCSP Stapling
CRLs and OCSP stapling are crucial components of a comprehensive security strategy. They provide mechanisms to verify that the certificate hasn’t been revoked.
- Certificate Revocation Lists (CRLs): A CRL is a list of revoked certificates. Clients consult CRLs to verify that the certificate presented by a server is still valid. A CRL will list all revoked certificates and is updated periodically. Failure to check the CRL can lead to a false sense of security if the certificate has been revoked.
- OCSP Stapling: OCSP stapling is a method for efficiently verifying certificate revocation status. Instead of clients querying a central OCSP server, the server provides the revocation status directly. OCSP stapling enhances performance and reduces the load on the OCSP server. This reduces the time it takes to verify the certificate, which improves security.
Advanced Topics
Securing your web server with SSL goes beyond basic setup. Advanced features enhance security, performance, and user experience. Understanding these features allows you to optimize your SSL configuration for maximum protection and efficiency.Implementing advanced SSL features like HTTP Strict Transport Security (HSTS) and proper cipher suite selection strengthens your website’s defenses against various attacks. Careful consideration of server-side certificate validation and configuring Apache for Server Name Indication (SNI) further enhances security and usability.
Finally, keeping your Apache server and SSL libraries updated is crucial for leveraging the latest security patches and improvements.
HTTP Strict Transport Security (HSTS)
HSTS is a crucial security mechanism that helps prevent man-in-the-middle attacks. It instructs browsers to only use HTTPS for future connections to a specific website.Browsers cache this information, ensuring future requests automatically use HTTPS. This policy strengthens your website’s security by preventing protocol downgrade attacks.
Cipher Suites and Protocols, Apache setup ssl certificate
Selecting appropriate cipher suites and protocols is essential for optimal security and performance. Modern cipher suites offer strong encryption while minimizing computational overhead.Using strong cryptographic algorithms and ensuring backward compatibility is key. Outdated protocols and cipher suites are vulnerable to exploits.
Server-Side Certificate Validation and Verification
Server-side certificate validation is a critical step in ensuring the authenticity of the server. Apache verifies the certificate’s validity by checking against a trusted Certificate Authority (CA) store.This process confirms the server’s identity, preventing man-in-the-middle attacks. Comprehensive validation protects users from fraudulent websites.
Configuring Apache for Server Name Indication (SNI) Support
Server Name Indication (SNI) allows multiple virtual hosts to use the same IP address and port while maintaining secure connections. This feature improves efficiency and simplifies hosting multiple domains on a single server.SNI is widely supported by modern browsers and is essential for handling virtual hosts securely. Configuring Apache for SNI is usually straightforward.
Keeping Apache and SSL Libraries Updated
Regular updates for Apache and its SSL libraries are vital for security. Security vulnerabilities are often discovered and patched in newer versions.Staying current with updates ensures your server utilizes the latest security patches and improvements. This proactive approach mitigates potential risks and enhances your overall security posture.
Concluding Remarks
In conclusion, securing your website with an SSL certificate is a critical step for building trust with visitors and ensuring data protection. This guide provided a comprehensive walkthrough of the Apache setup process, enabling you to confidently implement SSL on your server. Remember, security is an ongoing process, so regular maintenance and updates are key.