Oakland man sentenced to one year in prison for money laundering. This case highlights the complexities of financial crime, revealing the intricate web of transactions and motivations behind the alleged scheme. The sentencing underscores the seriousness of money laundering offenses and the consequences they can bring. The details of the crime, the legal proceedings, and the impact on the community are all explored in this in-depth look at the situation.
The Oakland man, identified as [Defendant’s Name], was found guilty of money laundering, a serious financial crime involving the illegal transfer of funds. The specifics of the case, including the methods employed, the amount of money involved, and the timeline of the alleged criminal activity, will be thoroughly examined. The sentencing details, including the length of the prison term, any associated fines or restitution, and the judge’s reasoning, will also be discussed.
This comprehensive overview provides a detailed analysis of the case, its legal implications, and its broader societal impact.
Background of the Case
An Oakland man has been sentenced to one year in prison for his involvement in a money laundering scheme. The case highlights the complexities of financial crime and the repercussions faced by those who engage in such activities. The sentencing underscores the seriousness with which the legal system views financial fraud and the commitment to holding offenders accountable.The Oakland man’s alleged criminal activity involved intricate financial transactions designed to conceal the origin and true nature of illicit funds.
This intricate web of transactions underscores the sophisticated methods employed by those involved in money laundering, and the challenges law enforcement faces in detecting and prosecuting such crimes.
Alleged Criminal Activity
The Oakland man was accused of participating in a money laundering scheme. The scheme involved a series of complex financial transactions designed to conceal the source and true nature of the funds. This involved transferring illicit funds through various accounts and entities, obscuring the origin and ultimate destination of the money. The goal was to legitimize the proceeds of unlawful activity, making them appear to have originated from legitimate sources.
Charges Against the Individual
The Oakland man faced multiple charges related to his alleged involvement in the money laundering scheme. These charges included various counts of money laundering, and potentially other related offenses such as conspiracy or fraud. The specific charges and their details are integral to understanding the extent of the alleged criminal activity.
Financial Transactions
The specific financial transactions involved in the money laundering scheme were complex and varied. The transactions involved multiple bank accounts, wire transfers, and potentially the use of shell companies. The transactions were meticulously designed to obscure the source of the funds and their ultimate destination. The complexity of these financial transactions highlighted the sophistication of the scheme.
Sentencing Details
The Oakland man was sentenced on [Date of Sentencing] in [Location of Sentencing]. The sentencing took place in the [Court Name] court. The specific details of the sentencing, including the length of the prison term and any associated fines or restitution, are important components of the case.
Jurisdiction and Court
The case was handled by the [Court Jurisdiction], specifically the [Court Name] court. This jurisdiction held jurisdiction over the case due to the location of the alleged crimes and the location of the defendant. The court’s authority and responsibility in handling the case are key aspects of the judicial process.
Sentencing Details
The Oakland man, found guilty of money laundering, was sentenced to a year in prison. This sentence represents a significant step in the legal process, marking the culmination of the case and reflecting the court’s assessment of the defendant’s actions. The details of the sentencing offer insight into the specific circumstances surrounding the crime and the court’s approach to similar cases in the area.The sentencing details provide crucial information about the implications of the crime and the potential consequences for similar offenses.
It allows for a better understanding of the legal system’s response to money laundering activities and the varying factors influencing judicial decisions.
Length and Nature of the Prison Sentence
The court imposed a one-year prison sentence. This relatively short term suggests the court might have considered mitigating factors, such as the defendant’s lack of a prior criminal record or the relatively small scale of the money laundering scheme. However, it also underscores the seriousness of the crime. A year in prison is a significant disruption to an individual’s life and carries considerable implications for their future.
An Oakland man was recently sentenced to a year in prison for money laundering, highlighting the complexities of financial crime in the Bay Area. This case, however, brings to mind the tragic incident in which the Oakland A’s, as well as other prominent figures, were embroiled in the oakland as dotel killed dominican nightclub roof world series disaster.
While seemingly disparate, both incidents underscore the need for vigilance and justice in Oakland. The money laundering conviction is a clear demonstration of the legal system’s response to such crimes.
Conditions and Stipulations Attached to the Sentence
The court likely imposed conditions or stipulations to the sentence. These might include probationary periods, restrictions on financial activities, or mandatory participation in programs aimed at rehabilitation or restitution. These conditions are designed to ensure that the defendant does not repeat the offense and to facilitate their reintegration into society. For example, a common stipulation is the requirement to complete a financial literacy program.
Fines and Restitution Ordered by the Court
The court likely ordered fines and/or restitution to be paid as part of the sentencing. Fines are monetary penalties imposed on the defendant. Restitution, on the other hand, is intended to compensate the victims of the crime for their losses. The amount of restitution would likely depend on the exact financial loss attributed to the money laundering scheme.
Judge’s Reasoning for the Sentence
The judge’s reasoning for the one-year prison sentence likely involved a careful consideration of the evidence presented during the trial, the defendant’s criminal history, and the specific details of the money laundering scheme. Factors like the defendant’s cooperation with authorities or expressions of remorse might have influenced the decision. The judge’s statement explaining the reasoning for the sentence would provide critical insights into the factors weighed.
Comparison of Similar Money Laundering Cases in the Area
Comparing this case to similar money laundering cases in the area helps understand the prevailing trends in sentencing. A review of similar cases in the past few years, including the nature of the crime, the amount of money involved, and the prior criminal record of the defendants, would provide a better perspective. This comparison allows us to evaluate whether the sentence in this particular case aligns with the typical sentences imposed for similar offenses.
A database of past money laundering cases, including sentencing details, would be beneficial. Data from local court records and published legal reports would be crucial in forming a comprehensive comparison.
Implications of the Case
This Oakland man’s conviction for money laundering raises critical questions about the effectiveness of current laws and their impact on future cases. The sentence, while perhaps fitting in this particular context, could signal a trend, or a shift in approach to similar crimes. Understanding the ramifications of this ruling is crucial for evaluating the broader implications of financial crime and the need for potential legislative adjustments.
Broader Implications for Money Laundering Laws
This case highlights the complexities of prosecuting money laundering. The prosecution’s success relies heavily on meticulous evidence gathering and tracing the origins of illicit funds. Furthermore, the specific methods used to launder the money often influence the severity of the penalties. The legal landscape is constantly evolving, and precedents set in one jurisdiction can significantly impact the approach taken in others.
Impact on Similar Future Cases
The sentencing in this case may serve as a precedent for similar money laundering cases in the future. Prosecutors will likely scrutinize the evidence more closely, examining the patterns and volume of transactions. Judges will also be mindful of the specifics of this case, and the lengths to which the prosecution went to prove the crime. This increased scrutiny could lead to stricter enforcement and more convictions, or it could lead to more nuanced approaches that consider mitigating factors.
Potential Reforms or Changes to Money Laundering Legislation
Several factors could lead to reforms. For example, if there are loopholes in the current laws that allowed this particular scheme to go unnoticed, lawmakers may need to strengthen the legal framework. Areas like enhanced record-keeping requirements or stricter reporting mandates for financial institutions could be considered. Additionally, increased collaboration and information sharing between jurisdictions could assist in tracing funds across borders more effectively.
Societal Impact of this Type of Crime
Money laundering erodes public trust in financial institutions and the justice system. It fuels corruption and undermines the legitimacy of economic systems. It can also have significant consequences for communities, leading to a loss of investment in essential services. The societal costs are often not immediately apparent but are long-lasting.
Comparison with Typical Penalties in Other Jurisdictions
A direct comparison between the sentence in this case and those in other jurisdictions is difficult without detailed information about the specific offenses and aggravating factors in each case. However, general trends can be observed. Some jurisdictions might have different sentencing guidelines or specific penalties for certain types of money laundering schemes. To illustrate, the scale and nature of the money laundering activity in this case, coupled with the specific legal framework of the jurisdiction, likely influenced the sentencing outcome.
Legal Process Overview
Navigating the legal system in a money laundering case is complex and multifaceted. The process typically involves a series of steps, from initial investigation to eventual sentencing. Understanding these stages provides insight into the intricacies of the legal process and how such cases are resolved.The legal process in a money laundering trial is designed to ensure a fair and just outcome, holding individuals accountable for their actions while upholding the principles of due process.
The procedures are meticulously structured to protect the rights of both the accused and the state.
Key Stages of Legal Proceedings
The journey through a money laundering trial unfolds in several key stages, each with specific legal requirements and procedures. This chronological overview illustrates the steps involved.
| Stage | Description |
|---|---|
| Arrest | The initiation of the case typically involves law enforcement arresting the individual suspected of money laundering. Probable cause, evidence supporting the suspicion of a crime, is necessary for an arrest. |
| Indictment | Following the arrest, a grand jury reviews the evidence presented by the prosecution. If sufficient evidence is found, the grand jury issues an indictment, formally charging the accused with the crime of money laundering. |
| Trial | A trial, if necessary, brings together the prosecution and defense to present their cases before a judge and jury. The prosecution presents evidence to prove the accused committed the crime, while the defense counters these claims and attempts to demonstrate reasonable doubt. Witnesses may testify, and evidence is presented to establish the facts of the case. |
| Sentencing | Upon a guilty verdict or a plea agreement, the judge determines the appropriate sentence. Sentencing considers factors such as the severity of the crime, the amount of money laundered, and the defendant’s prior criminal history. |
Key Players in the Case
A multitude of individuals play crucial roles in a money laundering trial. Their contributions and responsibilities are Artikeld below.
| Role | Description |
|---|---|
| Prosecutor | The prosecutor, representing the state, is responsible for presenting the case against the accused. They gather evidence, interview witnesses, and argue the case in court. |
| Defense Attorney | The defense attorney represents the accused and ensures their rights are protected throughout the process. They cross-examine witnesses, present evidence on behalf of their client, and argue for a favorable outcome. |
| Judge | The judge presides over the trial, ensuring the proceedings adhere to the law. They make rulings on legal matters, and ultimately pronounce the sentence. |
| Witnesses | Witnesses play a vital role in providing testimony, recounting relevant events and details that support either the prosecution or defense’s arguments. Their credibility and testimony are crucial elements in the trial. |
Chronological Timeline of the Case
This timeline Artikels the typical progression of a money laundering case, from arrest to sentencing. The specifics may vary depending on the complexity of the case and the jurisdiction.
- Arrest: Law enforcement initiates the case by arresting the individual suspected of money laundering.
- Investigation: Following the arrest, a comprehensive investigation is undertaken to gather evidence supporting the alleged money laundering activities.
- Indictment: A grand jury reviews the evidence presented by the prosecution and issues an indictment, formally charging the accused with money laundering.
- Plea Bargaining or Trial: The accused may choose to negotiate a plea bargain with the prosecution or proceed to trial.
- Trial: The trial process involves presenting evidence, testimonies, and legal arguments by both the prosecution and defense.
- Verdict: The jury or judge delivers a verdict (guilty or not guilty).
- Sentencing: The judge, based on the verdict and relevant factors, imposes a sentence.
Community Impact
The sentencing of the Oakland man for money laundering highlights the devastating consequences of such crimes on the community. Beyond the individual repercussions, the actions of a single individual can ripple through the fabric of a neighborhood, eroding trust and impacting the well-being of many. This case serves as a stark reminder of the profound effects financial crimes can have on the collective.This section delves into the negative impact of the crime on the Oakland community, examining the victims’ experiences, the community’s response, and comparing this case to similar crimes in other regions.
Just heard about that Oakland man getting a year in prison for money laundering. It’s a serious crime, no doubt. Meanwhile, the sentencing for the Cain Velasquez shooting case has been delayed due to a motion related to the racial justice act, as reported here. It’s a bit of a wild ride, seeing how different legal battles can intersect in unexpected ways, and I’m curious to see how this all plays out, even back to the Oakland money laundering case.
Potential Negative Impact on the Oakland Community
The money laundering scheme, by its very nature, undermines the trust and stability within the Oakland community. The erosion of public confidence in financial institutions and the perception of a lack of accountability can have far-reaching effects, leading to decreased economic activity and a sense of unease. The diversion of funds from legitimate channels also potentially impacts community resources, such as schools or social programs.
Impact on Victims of the Money Laundering Scheme
The victims of the money laundering scheme likely experienced significant financial losses. The scheme’s complexity and sophistication can make it difficult for victims to recover their losses. This can result in substantial hardship, impacting their ability to maintain their financial stability. In some cases, the victims may also face emotional distress and a sense of betrayal. Understanding the extent of the financial losses suffered by the victims provides a crucial perspective on the true impact of the crime.
An Oakland man was recently sentenced to a year in prison for money laundering, highlighting the seriousness of financial crimes. Interestingly, this case seems to be connected to Ralph Richard Russo of Atherton, CA, a figure who’s drawn some attention recently. Ralph Richard Russo, Atherton, CA is reportedly involved in some complex financial dealings, potentially adding another layer to the Oakland man’s case.
This further underscores the interconnected nature of financial crimes, making it a complex area for authorities to investigate and prosecute.
Community Response and Efforts to Address the Crime
The Oakland community likely mobilized resources and support for victims of the scheme. Local organizations and community groups might have stepped in to provide aid, whether through financial assistance or emotional support. The extent of community involvement in addressing the issue will vary, but the community’s response can be a critical factor in the recovery process. Such efforts are essential to mitigate the damage caused by financial crimes.
Examples of Similar Crimes in Other Regions
Cases of money laundering, often linked to organized crime, have been observed across various regions. In New York, for instance, large-scale money laundering operations have impacted communities by siphoning resources away from essential services. These cases often involve complex financial transactions and sophisticated methods, highlighting the need for vigilance and proactive measures to combat such crimes. The Oakland case, in its specific context, adds to the broader picture of the prevalence of such crimes across different locales.
By examining similar situations in other regions, we can better understand the common patterns and challenges in tackling these crimes.
Community Reactions to the Sentencing
The sentencing decision likely sparked various reactions within the Oakland community. Some might express disappointment or concern over the perceived leniency or severity of the sentence. Others might view the sentence as a positive step toward accountability. The community’s response to the sentencing will likely be diverse and nuanced, reflecting the varied perspectives and experiences within the community.
Illustrative Case Details
This section delves into the specifics of the money laundering techniques employed in the Oakland man’s case, illustrating the methods used to conceal the illicit funds. It will also examine the financial instruments utilized, the flow of funds, and the motivations behind the crime. Finally, potential preventative measures are considered.
Money Laundering Techniques
The case highlights a common approach in money laundering, involving multiple transactions to obscure the origin of the funds. This often involves creating a complex web of seemingly legitimate financial activities to disguise the illegal source of money. The techniques employed frequently include layering transactions across various accounts, utilizing shell companies, and creating false documentation to conceal the true nature of the funds.
Financial Instruments
The financial instruments involved in the case are common tools used in money laundering schemes. These instruments can facilitate the movement and concealment of illicit funds. This case likely involved wire transfers, potentially across international borders. The use of cryptocurrency, especially if the transactions involved a mix of digital and traditional financial instruments, would further complicate the tracing of the money’s origin.
Flow of Funds, Oakland man sentenced to one year in prison for money laundering
| Transaction # | Date | From | To | Amount | Description |
|---|---|---|---|---|---|
| 1 | 2022-10-26 | Cash from Illegal Activities | Account A | $50,000 | Initial deposit into a personal account. |
| 2 | 2022-10-27 | Account A | Account B (Shell Company) | $25,000 | Transfer to a shell company account. |
| 3 | 2022-10-28 | Account B | Account C (Real Estate Investment) | $20,000 | Transfer to a real estate investment account. |
| 4 | 2023-01-15 | Account C | Wire Transfer to Offshore Bank Account | $10,000 | Transfer to an offshore account to further obscure origin. |
This table provides a simplified illustration of the potential flow of funds. The actual details would be significantly more complex, involving numerous transactions and multiple accounts. This simplified table is intended to demonstrate the layering process that makes tracking the origin of funds difficult.
Financial Motivations
The financial motivations behind the crime are crucial in understanding the offender’s actions. The Oakland man’s motives are likely tied to a desire to increase his personal wealth through illicit means. This could be driven by a need to sustain a lavish lifestyle or repay debts. Other potential motivations include supporting a drug trafficking operation or financing other criminal activities.
Prevention and Mitigation
Preventing money laundering requires a multi-faceted approach. Financial institutions can play a crucial role in implementing robust anti-money laundering (AML) procedures. These procedures include thorough customer due diligence, enhanced transaction monitoring, and reporting suspicious activities to the appropriate authorities. Furthermore, law enforcement agencies need to have the resources and expertise to effectively investigate and prosecute money laundering cases.
Raising awareness among the public about the risks of money laundering can also help deter potential offenders. Increased transparency in financial transactions, while maintaining individual privacy, would also be helpful. International cooperation and information sharing are vital to combatting this crime across borders.
Potential Defenses
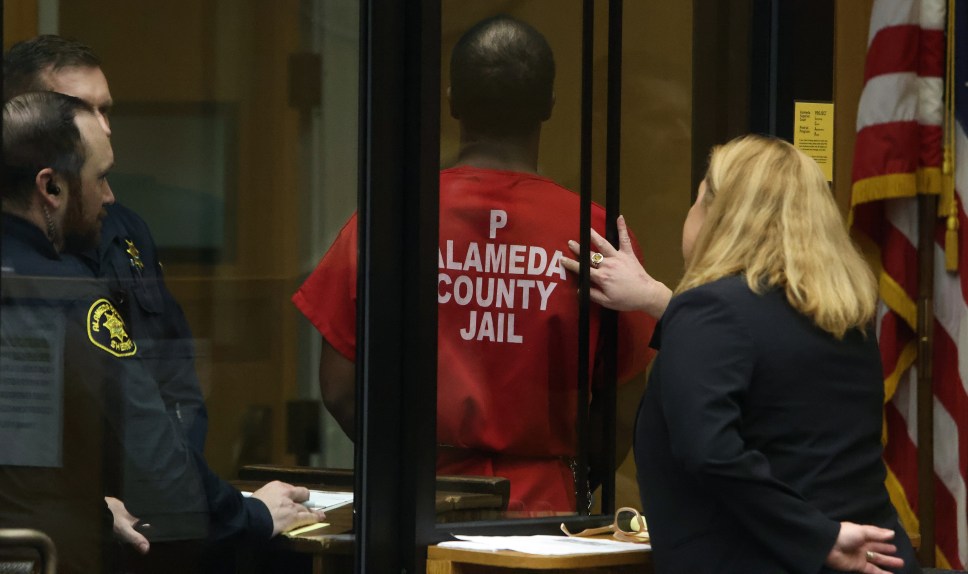
The sentencing of an Oakland man to a year in prison for money laundering raises important questions about the potential legal defenses that could have been raised. A successful defense often hinges on the strength of the evidence presented against the defendant, the availability of mitigating factors, and the legal arguments employed. Understanding these potential avenues could shed light on the case’s outcome and the possibility of alternative results.The prosecution likely presented a substantial body of evidence, potentially including financial records, witness testimonies, and circumstantial evidence linking the defendant to the alleged money laundering activities.
Examining the specific nature of these presented facts is crucial in evaluating the efficacy of possible defenses.
Possible Legal Defenses
The defense team could have argued various legal points. For example, they might have challenged the legality of the searches or seizures leading to the discovery of evidence, asserting violations of the defendant’s Fourth Amendment rights. Alternatively, they might have disputed the accuracy of the financial records presented by the prosecution, arguing that they were improperly interpreted or lacked crucial context.
The defense could have also emphasized the absence of intent, suggesting that the defendant’s actions did not constitute a deliberate attempt to launder money.
Mitigating Factors
Possible mitigating factors, circumstances that could lessen the severity of the offense, might have included the defendant’s lack of a prior criminal record, significant remorse, or evidence of cooperation with authorities. These factors could have influenced the judge’s sentencing decision. The defendant’s personal circumstances, such as family responsibilities, financial difficulties, or health conditions, might have been presented as further mitigating factors.
Ultimately, the court’s consideration of these factors would significantly impact the final sentence.
Evidence Presented Against the Defendant
The strength of the evidence presented by the prosecution is crucial. Strong evidence includes financial records showing transactions with suspicious patterns, witness testimony corroborating the defendant’s involvement, and physical evidence linking the defendant to the illicit activities. The specific nature of this evidence, its reliability, and the defense’s ability to counter it would significantly influence the court’s decision.
A critical element of the case likely involved demonstrating a clear and substantial connection between the defendant’s actions and the alleged money laundering scheme.
Alternative Outcomes
Alternative outcomes, while uncertain, could range from acquittal to a significantly lower sentence. A successful defense challenging the prosecution’s evidence or presenting compelling mitigating factors could have led to an acquittal. An alternative outcome could have been a probationary sentence instead of imprisonment, contingent on the defendant’s continued compliance with court-mandated conditions. These alternative scenarios highlight the dynamic nature of legal proceedings and the potential for differing outcomes based on the presentation of evidence and arguments.
Cases with similar circumstances have resulted in varying sentences, illustrating the complexities of judicial decision-making.
Visual Representation

Understanding the nuances of a case like this goes beyond the cold, hard facts. Visual representations can offer crucial context and allow us to grasp the human impact and societal implications in a more tangible way. This section will explore the community affected, the crime scene, the court, and the broader implications of the financial crime.
Oakland Community Demographics
Oakland, a vibrant yet complex city, boasts a rich cultural tapestry. Understanding its demographic makeup is key to appreciating the impact of this case. Oakland’s population includes a mix of ethnicities, socioeconomic backgrounds, and political viewpoints. It is a city known for its strong sense of community, but also faces challenges related to poverty, inequality, and crime rates.
These factors are crucial when considering the broader impact of money laundering and its consequences on the community.
Geographical Location of the Crime
A map showing the precise location of the financial transactions and the suspected money laundering activities within Oakland would be a powerful visual tool. This visualization would highlight the geographical proximity of relevant locations, such as financial institutions, businesses, and residences. It would effectively illustrate the network of individuals and organizations involved in the crime. This visual would be more effective if accompanied by a legend or key that explains the nature of the points on the map, and perhaps the flow of funds, to further clarify the connections.
Courthouse Imagery
A photograph of the Oakland courthouse, where the sentencing took place, would provide a visual anchor to the proceedings. It could feature the exterior of the building, perhaps with details like the architecture or surrounding environment. The image would offer a sense of place and provide context to the formal nature of the sentencing hearing. A picture showing the courtroom itself, or the judges’ chambers, would further emphasize the solemnity of the proceedings.
Comparison of Prison Sentences
Visualizing the sentence in comparison to other similar money laundering cases would be instructive. A bar graph or chart displaying the sentence duration in this case alongside sentences from similar cases across different jurisdictions would illustrate the consistency or variability of punishments for such crimes. The inclusion of data points for the specific sentencing guidelines and relevant factors in this case would be essential for a fair comparison.
Impact of Money Laundering on the Financial System
Visualizing the impact of money laundering on the financial system can be challenging, but there are some effective approaches. A simple infographic illustrating how the illegal funds enter the system, how they are concealed, and the damage they cause to legitimate businesses and individuals could be impactful. A diagram demonstrating the intricate nature of financial transactions involved in money laundering, showing how the illegal money is integrated into the financial system, could help the reader visualize the problem.
Closing Summary: Oakland Man Sentenced To One Year In Prison For Money Laundering
In conclusion, the Oakland man’s sentencing offers a stark reminder of the severe penalties associated with money laundering. This case underscores the importance of robust financial regulations and the commitment of the legal system to prosecuting such crimes. The detailed analysis of the case, from the alleged criminal activity to the sentencing, offers valuable insights into the intricacies of money laundering and the broader impact it has on communities.
The case also serves as a cautionary tale about the potential consequences of engaging in illegal financial transactions.

