What is phishing attack? It’s a deceptive practice used to steal sensitive information, often disguised as a legitimate communication. From emails mimicking banks to text messages posing as delivery services, phishing attacks leverage social engineering to trick unsuspecting victims into revealing passwords, credit card numbers, and other personal data. This intricate manipulation is a growing threat, and understanding how these attacks work is crucial for protecting yourself and your organization.
This article explores the various forms of phishing attacks, from the classic email scams to sophisticated targeted campaigns. We’ll delve into the methods used, the psychological tricks employed, and the devastating impact these attacks can have. Finally, we’ll equip you with the knowledge and tools to recognize and defend against phishing attempts, safeguarding your digital well-being.
Defining Phishing Attacks
Phishing attacks are a pervasive threat in today’s digital landscape. These malicious schemes prey on human psychology, exploiting our trust and carelessness to gain unauthorized access to sensitive information. Understanding the nuances of phishing is crucial for protecting yourself and your organization from these insidious attacks.Phishing is a deceptive practice where attackers masquerade as legitimate entities to trick victims into revealing confidential data, such as usernames, passwords, credit card details, and social security numbers.
The core objective of a phishing attack is to gain unauthorized access to sensitive information or to compromise systems for financial gain, espionage, or disruption. This is often achieved by manipulating victims into performing actions that grant the attacker access.
Phishing attacks are sneaky attempts to trick you into giving up your personal information, like passwords or credit card details. While scientists are busy exploring the potential of nasa asteroid samples watery world , it’s crucial to be vigilant about these online scams. Protecting your data is important, whether it’s discovering new worlds or just managing your daily online life.
Phishing Attack Methods
Phishing attacks employ a range of methods to deceive victims. These methods leverage human psychology, exploiting our trust and tendency to act quickly or impulsively. Critically, understanding these methods allows us to recognize and avoid these attacks.
- Deception through Fake Identities: Attackers often impersonate trusted organizations, such as banks, social media platforms, or government agencies, to instill confidence in the victim. This deception involves creating convincing copies of legitimate websites, emails, or other communication channels.
- Manipulation via Urgency and Fear: A common tactic is to instill a sense of urgency or fear in the victim, such as a threat of account suspension or a promise of a reward. This manipulation leverages our emotional responses to drive quick and impulsive actions.
- Social Engineering Exploits: Sophisticated phishing attacks utilize social engineering techniques to manipulate victims into revealing information or taking actions they might not otherwise undertake. This involves understanding the victim’s context and vulnerabilities to tailor the attack effectively.
Key Elements for a Successful Phishing Attack
The success of a phishing attack hinges on several key elements, which attackers meticulously craft to maximize their chances of success. Recognizing these elements is essential for developing effective defense mechanisms.
- Creating a Sense of Trust: Attackers meticulously design their communications to appear legitimate, mimicking the branding and style of reputable organizations. This trust-building process is fundamental to the attack’s success.
- Leveraging Psychological Manipulation: The exploitation of human emotions, such as fear, urgency, or greed, is a critical element of successful phishing attacks. This understanding of human behavior is central to the design of phishing attacks.
- Encouraging Immediate Action: Phishing attacks often create a sense of urgency, prompting victims to act quickly without fully considering the implications. This encourages impulsive actions, often leading to compromised accounts.
Common Phishing Techniques
Phishing attacks utilize various methods to deceive victims. Awareness of these techniques is crucial for effective defense.
- Email Phishing (Phishing): This is a prevalent method where attackers send deceptive emails that appear to be from legitimate organizations, requesting sensitive information or directing victims to malicious websites.
- Spear Phishing: A targeted approach, spear phishing focuses on specific individuals or organizations. Attackers research their victims to craft personalized messages, increasing the likelihood of success.
- Smishing (SMS Phishing): This involves sending deceptive text messages, often containing links to malicious websites or requests for personal information.
- Vishing (Voice Phishing): This method utilizes phone calls to impersonate legitimate organizations and trick victims into divulging sensitive information.
- Malicious Websites: These websites mimic legitimate ones, tricking victims into entering credentials or downloading malware.
Comparison of Phishing Methods
The following table provides a comparison of different phishing methods, highlighting their typical characteristics.
| Method | Target | Characteristics | Example |
|---|---|---|---|
| Email Phishing | Individuals | Fake emails, urgent tone, spoofed sender | A fake email from a bank requesting account details. |
| Spear Phishing | Specific individuals/organizations | Targeted attacks based on specific knowledge | A fraudulent email targeting a company executive with personalized details. |
Types of Phishing Attacks: What Is Phishing Attack
Phishing attacks are a multifaceted threat, employing various tactics to deceive victims. Understanding the different types of phishing attacks is crucial for recognizing and mitigating these threats. Each type leverages a specific approach, targeting individuals or organizations with varying degrees of specificity. Recognizing these nuances allows for tailored defenses and more effective security measures.
Deceptive Phishing
Deceptive phishing is the most common type of phishing attack. It aims to trick the victim into revealing sensitive information, such as usernames, passwords, or credit card details, by posing as a legitimate entity. This often involves creating fake websites or emails that mimic the appearance of trusted organizations.
- Common Tactics: These attacks often use spoofed email addresses and websites, mimicking legitimate companies or services. The goal is to trick the recipient into believing the communication is authentic.
- Examples: A common example is a fraudulent email pretending to be from a bank, asking the recipient to update their account details by clicking on a link to a fake website. Another example is a fake login page displayed on a compromised website that looks like the legitimate site.
Spear Phishing
Spear phishing attacks are more sophisticated than deceptive phishing. They target specific individuals or organizations, utilizing detailed information to personalize the attack and increase its effectiveness. The attacker researches the target’s interests, colleagues, and background to craft a more convincing and believable message.
- Common Tactics: Spear phishing attacks use highly personalized messages to increase the likelihood of the target clicking on malicious links or opening infected attachments. The attackers leverage publicly available information, social media profiles, and professional networks to tailor the attack to the victim.
- Examples: An example might involve an email from a seemingly legitimate colleague, requesting urgent access to a shared document or sensitive data. Another instance could be a phishing email impersonating a manager, asking for sensitive financial information.
Whaling
Whaling is a type of spear phishing attack specifically targeting high-profile individuals, such as CEOs, CFOs, or other senior executives. These attacks leverage the prestige and influence of the target to manipulate victims into revealing sensitive information.
- Common Tactics: Whaling attacks utilize highly targeted and personalized messages, often impersonating the victim’s superiors or trusted contacts. They often involve requests for large sums of money or access to sensitive information, leveraging the victim’s position within the organization.
- Examples: A CEO might receive a fake email supposedly from the company’s legal department, requesting immediate payment of a large sum to a fraudulent account. Another example is an email impersonating the company’s CEO, requesting sensitive financial data for a critical business transaction.
Table of Phishing Attack Types
| Type | Description | Example |
|---|---|---|
| Deceptive Phishing | Aims to trick the victim into revealing sensitive information by impersonating a legitimate entity. | Fake login page for a bank |
| Spear Phishing | Targets specific individuals or organizations by using personalized information. | Fake email from a known contact requesting urgent action. |
| Whaling | Targets high-profile individuals (CEOs, executives) with personalized attacks. | Fake email impersonating a CEO requesting sensitive financial data. |
Phishing Techniques
Phishing isn’t a single tactic; it’s a toolbox filled with various methods designed to trick victims into revealing sensitive information. These techniques often leverage psychological vulnerabilities and exploit social engineering principles to bypass a user’s natural defenses. Understanding these methods is crucial for recognizing and avoiding phishing attempts.Phishing techniques employ sophisticated strategies to manipulate individuals, leveraging psychological vulnerabilities and exploiting social engineering principles.
By understanding the tactics, individuals can enhance their awareness and improve their defenses against these sophisticated attacks.
Deceptive Email Phishing
Deceptive email phishing is the most prevalent form of phishing. It involves crafting emails that mimic legitimate communications from trusted sources, such as banks, social media platforms, or government agencies. These emails often contain urgent requests for personal information, financial details, or account access credentials. These messages aim to create a sense of immediate urgency or fear, prompting the recipient to act quickly without thinking critically.
- Spear Phishing: This technique targets specific individuals or organizations with highly tailored messages. Spear phishing emails appear highly personalized, leveraging specific information about the target to make the message more believable. For example, a spear-phishing email might reference a recent purchase or a pending transaction, using that information to trick the recipient into clicking a malicious link.
- Whaling: A more sophisticated form of spear phishing, whaling targets high-profile individuals, such as CEOs or executives. The attackers often collect extensive information about the target to create a highly convincing message. The goal is to compromise high-value accounts.
- Clone Phishing: This involves taking a legitimate email and modifying it to include malicious content, such as a harmful link or attachment. The attackers aim to replicate a genuine email, leading the recipient to believe it’s from a trustworthy source.
Malicious Links and Attachments
Malicious links and attachments are frequently used in phishing attacks. These links often lead to fraudulent websites designed to mimic legitimate platforms. These websites collect sensitive information from unsuspecting users. Attachments, such as malicious documents or executable files, can contain malware that compromises a user’s system or network.
- Fake Login Pages: Attackers create replica websites that look identical to legitimate banking sites or social media platforms. Victims are lured to these fake pages by phishing emails or malicious links, unknowingly entering their credentials into a fraudulent system.
- Malicious Attachments: Phishing emails may contain attachments masquerading as invoices, documents, or other legitimate files. These attachments might contain viruses, Trojans, or ransomware, which can infect a user’s system if opened.
SMS Phishing (Smishing) and Vishing
SMS phishing (smishing) and vishing (voice phishing) use text messages and phone calls to trick victims. Smishing messages often contain short, urgent requests for information, similar to email phishing. Vishing involves attackers posing as legitimate representatives, often from banks or tech support.
- Smishing: Smishing attacks employ text messages to mimic legitimate communications from financial institutions or other trusted organizations. The messages often contain urgent requests for personal information, leading the victim to click on a malicious link.
- Vishing: Vishing tactics involve using phone calls to impersonate legitimate authorities, such as banks or tech support. The attackers use deceptive techniques to gain trust and extract sensitive information.
Baiting and Quads
Baiting is a social engineering technique that uses something desirable to lure victims into a trap. This could be a free software download, a prize, or a coupon. Quad attacks are less common and use several methods to target individuals, potentially involving social media or even physical encounters.
- Baiting: Baiting tactics use tempting offers or prizes to encourage victims to download malware or provide sensitive information. A victim might be enticed to download a file promising a free game or software, unknowingly downloading malicious code.
- Quads: Quad attacks employ multiple tactics simultaneously to increase the chances of success. They might involve a combination of social engineering, email phishing, and other techniques to create a more convincing attack.
Impact of Phishing Attacks
Phishing attacks, while seemingly simple, can have devastating consequences for individuals and organizations. The potential damage extends far beyond a mere inconvenience; it can lead to significant financial losses, reputational damage, and even the compromise of sensitive data. Understanding the multifaceted impact of these attacks is crucial for effective prevention and mitigation strategies.
Financial Losses, What is phishing attack
Phishing attacks often exploit human psychology to trick victims into revealing sensitive information like usernames, passwords, credit card details, and bank account information. This stolen data is then used for fraudulent transactions, leading to substantial financial losses for both individuals and organizations. A common example involves a victim clicking on a malicious link in an email, which redirects them to a fake login page designed to capture their credentials.
Once compromised, the attacker can drain bank accounts, make unauthorized purchases, or open fraudulent accounts in the victim’s name. The financial losses can range from small amounts to considerable sums, depending on the scope of the attack and the victim’s financial situation.
Phishing attacks are sneaky attempts to steal your personal info, like passwords and credit card details. They often involve fake emails or websites that look incredibly real. It’s crucial to be cautious about links and attachments, especially if they seem suspicious. Think of how important it is to configure your Windows settings correctly, like using sticky keys in windows , for accessibility.
These measures, just like recognizing phishing attempts, are vital for online security. Always double-check the sender and the content before clicking anything.
Reputational Damage
Organizations that fall victim to phishing attacks face significant reputational damage. Loss of customer trust is a direct consequence, as victims may perceive the organization as negligent or incapable of protecting their data. The ensuing negative publicity can severely impact the organization’s brand image and market share. For example, a major retail chain that experiences a widespread phishing attack could see a sharp decline in customer loyalty and sales as consumers lose faith in the company’s security measures.
The extent of reputational damage depends on the scale of the incident and the effectiveness of the organization’s response.
Data Breaches
Phishing attacks often serve as a gateway to more significant data breaches. Compromised credentials can unlock access to sensitive organizational data, including customer information, intellectual property, and financial records. This unauthorized access can have far-reaching consequences, impacting both the organization and its customers. For instance, a healthcare provider that suffers a phishing attack resulting in a data breach could face significant legal repercussions and financial penalties for the exposure of patient records.
The severity of the data breach is contingent on the type and volume of data compromised.
Emotional Toll on Victims
The emotional impact of phishing attacks should not be underestimated. Victims may experience feelings of betrayal, anxiety, and stress, particularly when financial or personal information is stolen. The fear of identity theft, financial ruin, and the emotional toll on victims is a critical aspect of understanding the full impact of phishing attacks. For example, an individual who loses their savings due to a phishing attack might experience significant financial hardship and emotional distress.
Table of Impacts
| Impact | Description | Example |
|---|---|---|
| Financial Loss | Loss of money due to fraudulent transactions | Stolen credit card details leading to unauthorized purchases. |
| Data Breach | Sensitive data exposure | Stolen personal information, compromising customer records. |
| Reputational Damage | Damage to the reputation of an organization | Loss of customer trust, leading to a decline in sales. |
Protecting Yourself from Phishing Attacks
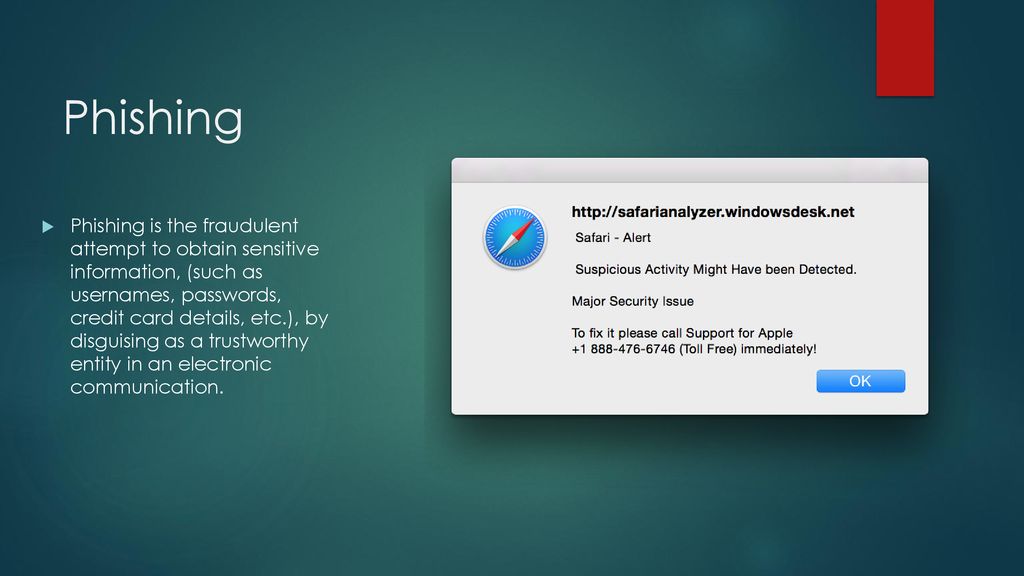
Phishing attacks are a constant threat in today’s digital landscape. Knowing how to recognize and avoid these scams is crucial for protecting your personal information and financial security. Understanding the methods used by phishers allows you to proactively safeguard yourself and your loved ones. This knowledge empowers you to spot suspicious activities and react appropriately.Recognizing suspicious patterns is the first line of defense against phishing attempts.
Look for inconsistencies in the communication you receive, whether it’s an email, a text message, or a phone call. This vigilance helps you to avoid falling prey to fraudulent schemes.
Recognizing Phishing Attempts
Phishing attempts often use deceptive tactics to trick you into revealing sensitive information. They frequently mimic legitimate organizations or individuals, creating a sense of urgency or trust. This impersonation can lead to a loss of your valuable data. Pay close attention to the details of the communication. Look for inconsistencies in the sender’s email address, the tone of the message, or the request itself.
These inconsistencies are crucial clues in identifying a phishing attempt.
- Look for poor grammar and spelling errors. Phishing emails often contain mistakes that a legitimate organization would avoid.
- Examine the sender’s email address carefully. Is it a plausible address for the purported sender? Does it match the official website’s domain name?
- Be wary of urgent requests for personal information. Legitimate organizations rarely demand sensitive data via email or text messages.
- Verify the URL of any links provided. Hover over the link before clicking to see the actual destination address. Look for suspicious or unexpected characters in the URL.
Verifying Email Addresses and Links
Thorough verification of email addresses and links is essential for preventing phishing attacks. Always scrutinize the sender’s email address to ensure it matches the official domain of the organization or individual. This verification helps avoid scams. Double-checking links is equally critical. Never click on links in emails unless you’re absolutely certain of their legitimacy.
Always check the actual URL by hovering your mouse over the link before clicking.
- Look for misspellings or variations of the official domain name in the sender’s email address. This is a common technique used by phishers.
- Avoid clicking on links that look suspicious or unexpected. Instead, visit the official website directly through a search engine or a bookmark.
- Use a different browser window or tab to visit the site mentioned in the email. If possible, verify the contact information on the official website, which may help in determining if the email is authentic.
Strong Passwords and Multi-Factor Authentication
Strong passwords and multi-factor authentication (MFA) are vital security measures. Use a unique, complex password for each account and avoid using easily guessed passwords. Employing MFA adds an extra layer of security, requiring more than just a password to access your accounts. This additional verification significantly enhances your protection against unauthorized access.
- Use a password manager to create and store strong, unique passwords for different accounts.
- Enable multi-factor authentication (MFA) whenever possible for your online accounts. MFA adds an extra layer of security by requiring a second verification method.
- Choose strong passwords that are difficult to guess. Avoid using personal information or easily recognizable words in your passwords.
Security Awareness Training
Regular security awareness training is a crucial aspect of protecting yourself from phishing attacks. This training provides essential information about recognizing phishing attempts and avoiding common traps. Training helps you stay informed about the latest techniques used by phishers. It equips you with the knowledge to make informed decisions when interacting with suspicious communications.
Phishing attacks are sneaky attempts to trick you into giving away personal information, like passwords or credit card details. It’s like a con artist trying to steal your identity. Finding where to watch your favorite NHL games can be tricky too, sometimes websites look super legitimate, but they aren’t! For a full guide on where to catch all the NHL action, check out this great resource on nhl games where to watch.
Ultimately, always be wary of suspicious emails or messages, and double-check any links before clicking them, to avoid falling prey to these online scams.
- Stay informed about current phishing trends and techniques. This knowledge helps you recognize and avoid the latest tactics used by phishers.
- Enroll in security awareness training programs offered by your organization or other reputable sources.
- Discuss phishing awareness with your family and friends to protect everyone.
Step-by-Step Guide for Identifying Phishing Emails
- Check the sender’s email address: Carefully examine the sender’s email address. Verify that it matches the official domain of the organization or individual. Look for misspellings or variations of the official domain name.
- Inspect the email content: Review the email content for urgent requests for personal information, poor grammar, or unusual language. Pay attention to the tone of the message and any threats.
- Examine the links: Hover over any links in the email before clicking them to see the actual URL. Look for suspicious or unexpected characters in the URL. Avoid clicking on links that look suspicious or unexpected.
- Verify the request: If the email requests personal information, contact the organization or individual directly through a known and trusted channel to confirm the request.
- Report suspicious emails: If you suspect an email is a phishing attempt, report it to the appropriate authorities.
Measures to Prevent Phishing Attacks

Phishing attacks remain a significant threat to organizations and individuals alike. Implementing robust preventive measures is crucial for mitigating risks and safeguarding sensitive information. Effective strategies encompass a multi-faceted approach, integrating technical solutions, security awareness training, and clear employee guidelines. A proactive stance is essential in combating this ever-evolving form of cybercrime.Organizations can significantly reduce their vulnerability to phishing attacks by proactively addressing the various vectors through which these attacks manifest.
This involves a layered approach, incorporating technology, training, and clear policies. By combining these elements, organizations can create a formidable defense against phishing attempts, safeguarding their valuable assets and reputation.
Technical Solutions for Phishing Prevention
Implementing strong technical safeguards is paramount in preventing phishing attacks. These solutions act as the first line of defense, identifying and blocking suspicious communications before they reach employees.
- Email Filtering and Spam Blocking: Sophisticated email filters can identify and block phishing emails based on various criteria, including sender reputation, suspicious content (malicious links, attachments, or unusual language), and blacklisted IP addresses. These filters significantly reduce the likelihood of phishing emails reaching employees’ inboxes.
- Web Filtering and URL Scanning: Web filtering solutions can prevent users from accessing malicious websites. These systems proactively scan URLs and block access to known phishing websites, stopping users from clicking on dangerous links.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security to accounts. Even if a malicious actor gains a user’s password, they still need a second authentication factor (like a code sent to a mobile phone) to access the account. This makes it significantly harder for attackers to gain unauthorized access.
- Data Loss Prevention (DLP) Systems: DLP systems monitor and control sensitive data to prevent its unauthorized disclosure. These systems can identify and block the transfer of sensitive information via email, instant messaging, or other channels. This approach helps to stop the flow of compromised data, which is crucial in phishing attacks.
Security Awareness Programs and Training
Employee training is a crucial component in preventing phishing attacks. A well-designed security awareness program can empower employees to recognize and report suspicious activities, forming a human firewall against phishing attempts.
- Regular Training Sessions: Regular training sessions are essential to keep employees updated on the latest phishing techniques and strategies. This includes recognizing different types of phishing attacks, identifying suspicious emails, and reporting potential threats to the appropriate channels.
- Interactive Simulations: Interactive simulations can create a realistic phishing attack scenario. These exercises allow employees to practice their skills in recognizing and responding to phishing attempts in a risk-free environment, building their resilience against such attacks.
- Gamification and Incentives: Introducing gamification and incentives to training can increase employee engagement and motivation. This can involve awarding points or prizes to employees who successfully identify phishing attempts or participate in training activities.
Best Practices for Employees
Establishing clear guidelines for employees can significantly reduce the risk of falling victim to phishing attacks. This involves clear expectations, consistent procedures, and accountability for actions.
- Verify Requests: Employees should always verify requests for sensitive information via phone calls or official communication channels, instead of relying on emails or messages that seem suspicious.
- Hover Before Clicking: Employees should always hover their mouse over links before clicking them to examine the destination URL. This can help to identify shortened links that lead to malicious websites.
- Report Suspicious Activity: A critical step is for employees to report any suspicious emails, messages, or websites to the IT department or security team immediately. This enables swift action to mitigate potential damage.
Examples of Successful Phishing Prevention Strategies
Several organizations have implemented successful phishing prevention strategies, demonstrating the effectiveness of a proactive approach. These strategies often combine technical solutions, training, and clear policies.
- Company X implemented a multi-layered approach that included robust email filtering, regular security awareness training, and a clear reporting procedure. This strategy significantly reduced phishing attempts and improved employee vigilance.
- Company Y implemented a comprehensive web filtering solution that blocked access to known phishing websites. Combined with regular security awareness training, this approach prevented numerous potential attacks.
Ultimate Conclusion
In conclusion, phishing attacks are a pervasive and evolving threat. Understanding the different types, techniques, and impacts is the first step towards effective protection. By recognizing the signs of a phishing attempt, employing strong passwords and multi-factor authentication, and staying informed about emerging tactics, you can significantly reduce your vulnerability. Protecting yourself and your organization from phishing requires ongoing vigilance and a proactive approach to security.

