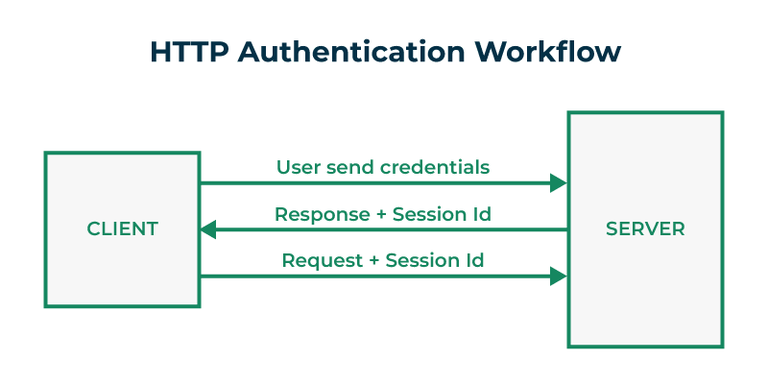
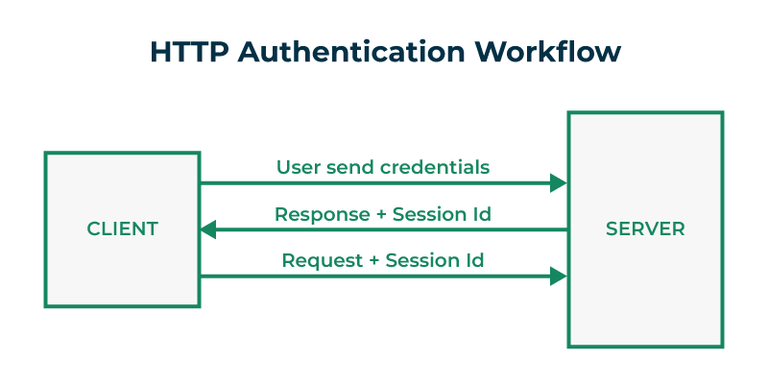
Securing Flask API with JWT: A comprehensive guide delves into the intricacies of securing your Flask APIs using JSON Web Tokens (JWTs). This involves understanding the critical importance of API security, common vulnerabilities, and the pivotal role JWTs play in securing your application. We’ll cover the implementation process, explore the Flask-JWT-Extended library, delve into authorization techniques, and handle potential errors effectively.
Finally, best practices and advanced considerations will round out your knowledge of securing your Flask API.
This in-depth exploration will walk you through setting up JWT authentication, generating and verifying tokens, and implementing authorization rules. We’ll provide clear code examples, detailed explanations, and helpful tables to aid in your understanding and implementation. The ultimate goal is to equip you with the knowledge and tools to build a robust and secure Flask API.
Introduction to Flask API Security
Flask APIs, while offering a lightweight and flexible framework for building web applications, are susceptible to various security threats if not properly protected. Protecting your API from malicious attacks is crucial for maintaining data integrity, user trust, and the overall stability of your application. A compromised API can lead to data breaches, unauthorized access, and potential financial losses.A robust security strategy is essential to mitigate these risks.
This involves understanding the common vulnerabilities, implementing appropriate security measures, and utilizing tools to monitor and detect potential threats. JWTs play a pivotal role in enhancing API security by providing a secure way to authenticate users and authorize access to protected resources.
Common Security Vulnerabilities in Flask APIs
Understanding the common vulnerabilities in Flask APIs is the first step towards securing them. These vulnerabilities can range from simple coding errors to more sophisticated attacks. Addressing these issues proactively helps prevent potential breaches and ensures data safety.
Securing your Flask API with JWTs is crucial for protecting user data. It’s all about adding that extra layer of security, just like upgrading your kitchen appliances. For example, if you’re looking to whip up delicious meals in these convection ovens, whip up delicious meals in these convection ovens , you’d want to ensure the oven’s controls are secure.
Similarly, robust API security with JWTs is essential for safeguarding sensitive information in your applications.
- Injection Attacks: SQL injection, command injection, and cross-site scripting (XSS) are common vulnerabilities where malicious inputs can be used to manipulate the application’s logic or gain unauthorized access. Careful input validation and parameterized queries are vital to prevent these attacks.
- Cross-Site Request Forgery (CSRF): CSRF attacks trick users into performing unwanted actions on a web application. Implementing CSRF protection measures, such as using tokens, is essential to prevent these attacks.
- Authentication and Authorization Issues: Weak or missing authentication mechanisms can allow unauthorized users to access sensitive data or perform actions they are not permitted to. Proper authentication using secure passwords and robust authorization mechanisms are crucial.
- Insufficient Input Validation: Unvalidated inputs can be exploited to perform malicious actions, like denial-of-service attacks or data breaches. Thorough validation of all user inputs is essential to prevent exploitation.
The Role of JWTs in API Security
JSON Web Tokens (JWTs) are compact, self-contained packets of information that are exchanged between parties as a secure method of authentication. They are signed using cryptographic signatures, making them ideal for secure communication in APIs.
- Authentication and Authorization: JWTs can efficiently convey authentication information, such as user identity and roles, within the API requests. This information can then be used to authorize access to specific resources.
- Reduced Server Load: JWTs allow the client to carry authentication information without requiring repeated communication with the server. This reduces the server’s workload and improves performance.
- Improved Security: The cryptographic signature ensures the integrity and authenticity of the token, minimizing the risk of tampering or impersonation. This enhanced security is crucial in preventing unauthorized access.
Basic Flask API Structure for Demonstration, Securing flask api with jwt
A well-structured Flask API demonstrates best practices for security and maintainability. This structure provides a foundation for further development and customization.“`pythonfrom flask import Flask, request, jsonifyfrom flask_jwt_extended import JWTManager, create_access_token, get_jwt_identityapp = Flask(__name__)app.config[‘SECRET_KEY’] = ‘your_secret_key’ # Replace with a strong keyjwt = JWTManager(app)@app.route(‘/login’, methods=[‘POST’])def login(): auth = request.get_json() # … (Authentication logic) …
access_token = create_access_token(identity=user_id) # Replace with actual user ID return jsonify(‘access_token’: access_token), [email protected](‘/protected’, methods=[‘GET’])@jwt_required()def protected(): current_user = get_jwt_identity() # … (Protected resource logic) … return jsonify(‘message’: ‘Protected resource accessed’), 200“`This example demonstrates a basic structure for a Flask API, including a login endpoint and a protected resource endpoint secured by JWTs.
It highlights the crucial role of `flask_jwt_extended` for token management. Remember to replace placeholders like `user_id` and the secret key with actual implementation details.
Implementing JWT Authentication
Securing your Flask API with JSON Web Tokens (JWTs) is crucial for protecting sensitive data and ensuring authorized access. JWTs provide a standardized way to transmit security information between parties, enabling secure communication between your API and clients. This method eliminates the need for sending credentials with each request, enhancing efficiency and security.Implementing JWT authentication involves a three-part process: generating tokens, sending them to clients, and verifying the tokens on the server-side.
This process allows for secure and efficient communication. The Python library `PyJWT` is a popular choice for handling JWTs, offering straightforward methods for generating and verifying tokens.
Generating JWTs
The process of generating a JWT involves creating a payload containing the necessary user information, signing it using a secret key, and encoding it into a compact, URL-safe string. This process ensures that the token cannot be easily modified or forged. This is a fundamental step for securing your API.
- Construct the payload: The payload is a dictionary containing claims about the user. Crucially, this includes information like the user’s ID, roles, or other relevant data.
- Sign the payload: The payload is signed using a secret key to create a digital signature. This signature verifies the token’s integrity and authenticity. The secret key should be kept securely.
- Encode the token: The signed payload is encoded into a compact, URL-safe string. This string is the JWT, which can then be sent to the client.
Verifying JWTs
The server-side verification process ensures that the received token is valid and trustworthy. This step is essential to prevent unauthorized access to your API.
- Decode the token: The received JWT is decoded into its constituent parts, including the header, payload, and signature.
- Verify the signature: The decoded signature is compared to the one generated from the header and payload. If they match, the token is deemed authentic.
- Extract claims: The payload is extracted and used to validate the user’s identity and access level.
Using PyJWT
PyJWT simplifies the process of generating and verifying JWTs. This library provides a straightforward API for handling tokens.
| Step | Description |
|---|---|
| 1 | Import the necessary classes from PyJWT: from pyjwt import JWT. |
| 2 | Create a secret key. This key should be kept securely. |
| 3 | Construct the payload dictionary: payload = 'user_id': 123, 'exp': datetime.utcnow() + timedelta(minutes=30). Important data such as expiration times (exp) are essential for security. |
| 4 | Generate the JWT: token = JWT.encode(payload, secret_key, algorithm='HS256'). |
| 5 | Verify the JWT: decoded_token = JWT.decode(token, secret_key, algorithms=['HS256']). |
Example: “`pythonfrom pyjwt import JWTfrom datetime import datetime, timedeltaimport base64secret_key = ‘your_secret_key’ # Replace with a strong secret keypayload = ‘user_id’: 123, ‘exp’: datetime.utcnow() + timedelta(minutes=30)token = JWT.encode(payload, secret_key, algorithm=’HS256′)decoded_token = JWT.decode(token, secret_key, algorithms=[‘HS256’])print(decoded_token)“`
This example demonstrates a basic JWT implementation in Flask. Remember to replace `’your_secret_key’` with a strong, randomly generated secret key. Appropriate error handling is crucial in production code to gracefully manage invalid or expired tokens.
Flask-JWT-Extended Library
Flask-JWT-Extended builds upon the foundational JWT authentication, providing a more comprehensive and feature-rich solution for securing Flask APIs. It simplifies the implementation of various authentication scenarios, enhances security features, and allows for more sophisticated custom claims within JSON Web Tokens. This library offers significant advantages over basic JWT implementation by abstracting away complex details and providing convenient functionalities.
Key Functionalities
Flask-JWT-Extended provides an array of functionalities beyond basic JWT generation and verification. It handles token expiration, refresh tokens, custom claims, and user loading strategies, significantly reducing the amount of code needed for a robust authentication system. This robust toolkit streamlines the development process and ensures better security.
Implementing Authentication Scenarios
This library allows for various authentication scenarios, from simple user login to more complex scenarios involving refresh tokens. The library handles the intricacies of token management and allows developers to focus on application logic.
- User Login: Flask-JWT-Extended simplifies the process of generating access tokens upon successful login. The library handles token creation and provides methods to return tokens in a standard format for client use.
- Refresh Tokens: The library facilitates the creation and management of refresh tokens, enabling users to obtain new access tokens without re-authenticating. This improves user experience and security.
Creating Custom Claims
Flask-JWT-Extended empowers developers to add custom claims to JWTs. These claims can be used to store specific user information, permissions, or other relevant data. This functionality provides the flexibility to incorporate domain-specific data into the JWT.
- Example: A custom claim for user role could be added, allowing the API to dynamically adjust access based on the user’s role. For example, a claim like
"role": "administrator"could be added to a JWT, indicating the user’s role to the application.
Benefits and Drawbacks
Flask-JWT-Extended offers several benefits over other JWT implementations. It streamlines the authentication process, enhances security, and provides a comprehensive toolkit.
- Benefits: Enhanced security features, simplified implementation, better token management, and improved user experience.
- Drawbacks: Learning curve for new users, increased complexity in comparison to simpler libraries, potential performance overhead if not optimized properly.
Configuration
Correct configuration is essential for leveraging Flask-JWT-Extended effectively. Proper configuration ensures the security and functionality of the authentication system.
| Configuration Setting | Description |
|---|---|
SECRET_KEY |
A secret key used for signing and verifying JWTs. Crucial for security, it should be a long, randomly generated string. |
JWT_SECRET_KEY |
(Recommended) A separate secret key specifically for JWTs. This separation enhances security. |
JWT_EXPIRATION_DELTA |
Sets the time duration for which access tokens are valid. |
JWT_REFRESH_TOKEN_EXPIRATION_DELTA |
Sets the time duration for which refresh tokens are valid. |
JWT_IDENTITY_CLAIM |
Defines the claim containing user identity. |
Handling Authorization
Securing your Flask API goes beyond just authentication. Authorization determines what actions a user, identified by their token, is permitted to perform. This crucial step ensures that only authorized users can access specific resources or execute particular operations. This section details the process of implementing authorization rules within a Flask API, offering various schemes and practical examples.Authorization, in essence, adds a layer of control above authentication.
While authentication verifies a user’s identity, authorization verifies their right to access a particular resource. Without proper authorization, even authenticated users could potentially misuse or exploit the API.
Role-Based Authorization
Role-based authorization is a common and effective approach. It assigns users to roles, and each role has specific permissions associated with it. This approach promotes organization and maintainability, especially in large applications with multiple users and varying access needs.
- Defining Roles: Create a list of roles, such as ‘administrator’, ‘editor’, ‘viewer’. Each role should have a predefined set of permissions.
- Associating Roles with Users: Store the user’s assigned role in your database alongside their user information.
- Checking Permissions: When a user attempts to access a resource, check their associated role against the required permissions for that resource.
Example Implementation (Flask-JWT-Extended)
“`pythonfrom flask import Flask, requestfrom flask_jwt_extended import ( JWTManager, jwt_required, get_jwt_identity, get_raw_jwt)import datetime# … (other imports and app initialization) …@app.route(‘/protected_resource’, methods=[‘GET’])@jwt_requireddef protected_resource(): current_user_role = get_user_role(get_jwt_identity()) # Function to retrieve role required_role = ‘editor’ # Resource permission if current_user_role == required_role: return jsonify(‘message’: ‘Access granted’), 200 else: return jsonify(‘message’: ‘Forbidden’), 403def get_user_role(user_id): # Replace with your database logic user_data = User.query.filter_by(id=user_id).first() if user_data: return user_data.role else: return None # Or raise an exception“`This example demonstrates a basic role-based check.
The `get_user_role` function retrieves the user’s role from a database (replace with your database interaction logic).
Custom Authorization Functions
Custom authorization functions offer flexibility for complex access control scenarios. These functions can encapsulate specific logic for verifying permissions beyond simple role checks.
- Flexibility: Handle cases not covered by predefined roles.
- Reusability: Create reusable authorization functions that can be applied across multiple endpoints.
Comparison of Authorization Methods
| Method | Description | Advantages | Disadvantages |
|---|---|---|---|
| Role-Based | Users assigned to roles, each with permissions | Simple, organized, maintainable | Can be inflexible for complex permissions |
| Attribute-Based | Based on user attributes (e.g., location, group membership) | Highly customizable | Can be complex to implement and manage |
| Custom Functions | Specific logic for verifying permissions | Maximum flexibility | Requires more development effort |
Error Handling and Response Management
Robust error handling is crucial for any API, especially when dealing with authentication. It ensures a smooth user experience, prevents unexpected crashes, and allows for effective debugging. Properly formatted error responses provide essential information to clients, enabling them to understand the issue and take appropriate action. This section dives into best practices for handling authentication errors and crafting informative responses for your Flask API secured with JWTs.
Authentication Error Handling
Effective error handling for authentication errors, such as invalid or expired JWTs, prevents silent failures and provides meaningful feedback to clients. By clearly defining and returning specific error responses, you enhance the reliability and usability of your API.
Error Response Formats
A well-structured error response clearly communicates the nature of the problem to the client. Different formats are possible, but consistency is key. A JSON structure is commonly used, containing a descriptive error message, a unique error code, and any relevant details for debugging.
- JSON Example (Success):
“`json“status”: “success”,
“message”: “Authentication successful”,
“data”: “user_id”: 123, “user_name”: “john_doe”Securing Flask APIs with JWTs is crucial for protecting sensitive data. One important aspect is understanding the intricacies of authentication and authorization. Knowing how to properly implement JWTs can greatly improve the security of your API, which is especially relevant when considering the public figure of Clifford Burrous in Santa Clara, CA. Clifford Burrous Santa Clara CA highlights the importance of robust online security measures.
Ultimately, securing your Flask API with JWTs is a key part of building a reliable and trustworthy web application.
“`
- JSON Example (Failure):
“`json“status”: “failed”,
“error”:
“code”: “invalid_token”,
“message”: “The provided JWT is invalid or expired.”“`
Importance of Proper Error Handling
Proper error handling in APIs is paramount. It minimizes the risk of unexpected behavior, enhances the user experience, and aids in debugging. Consider the impact of a poorly handled authentication error—a user might be blocked from accessing resources, or worse, sensitive data could be compromised. By providing clear and concise error messages, you empower users to rectify the issue, preventing frustration and enhancing the overall reliability of your API.
Response Structure for Authentication
A standardized response structure for authentication attempts, both successful and failed, improves the consistency and readability of your API. This structure ensures that clients receive a predictable format for all responses, regardless of the outcome.
- Successful Authentication Response:
The response should include a success status, a message indicating successful authentication, and potentially user data. - Failed Authentication Response:
The response should include a failure status, a specific error code and message, and potentially any additional details for troubleshooting. It’s critical to avoid exposing sensitive information in error messages to prevent potential security vulnerabilities.
Error Type Table
The table below Artikels different error types that might occur during authentication and their corresponding response codes and descriptions.
| Error Type | Response Code | Description |
|---|---|---|
| Invalid JWT | 401 | The provided JWT is invalid or malformed. |
| Expired JWT | 401 | The provided JWT has expired. |
| Missing JWT | 401 | No JWT was provided in the request. |
| Incorrect Credentials | 401 | The provided credentials (username/password) are incorrect. |
Security Best Practices
Securing a Flask API with JWTs goes beyond just implementing authentication. Robust security requires a layered approach, encompassing secure storage of secrets, careful session management, and proactive measures to prevent common pitfalls. This section details crucial best practices to bolster the security of your API.Implementing strong security measures is vital to protect sensitive data and maintain user trust. This involves a proactive approach to anticipate potential threats and vulnerabilities, mitigating risks before they can be exploited.
Secure Storage of API Secrets
Storing API secrets, such as API keys and encryption keys, is paramount. Never hardcode these sensitive values directly into your code. Instead, utilize environment variables. This approach isolates sensitive data from the codebase, making it more resistant to accidental exposure or malicious code injection.
- Employ environment variables to store sensitive information. This practice significantly enhances security by separating critical data from the application code. The values can be set during development or deployment in a controlled environment.
- Utilize a secrets management service for production deployments. Services like AWS Secrets Manager, Azure Key Vault, or HashiCorp Vault offer secure storage and retrieval of secrets, reducing the risk of breaches.
- Implement proper access controls to limit access to environment variables. Restrict access to only authorized personnel or systems.
Secure Session Management
Secure session management is crucial for preventing unauthorized access to user data and protecting against session hijacking attacks. JWTs, when implemented correctly, facilitate secure session management. Avoid storing sensitive information directly in the session.
- Use short-lived JWTs. This reduces the window of opportunity for attackers to exploit compromised tokens. Revoking and rotating tokens promptly can minimize the impact of potential breaches.
- Implement token revocation mechanisms. This allows you to invalidate tokens if a user’s account is compromised or if they log out.
- Employ secure HTTP headers. Using the `Set-Cookie` header with the `HttpOnly` flag prevents JavaScript access to cookies, reducing the risk of cross-site scripting (XSS) attacks.
Avoiding Common Security Pitfalls
Several common pitfalls can compromise the security of your Flask API. Proactive measures can prevent these issues.
- Validate all user inputs. Prevent malicious code injection by meticulously validating data received from clients. Use appropriate data sanitization techniques to remove or escape potentially harmful characters.
- Restrict API endpoints. Use appropriate HTTP methods (e.g., GET, POST, PUT, DELETE) and authentication mechanisms to control access to specific API endpoints.
- Employ rate limiting. Prevent abuse and denial-of-service attacks by limiting the number of requests a user can make within a specific timeframe.
Secure Logging
Implementing secure logging is essential for debugging and auditing. However, logging sensitive data can pose a security risk. Restrict log entries to only relevant information.
- Log only necessary information. Avoid logging sensitive data like passwords or API keys. Use placeholders or redactions for sensitive information.
- Implement proper log rotation. Regularly rotate logs to prevent log files from becoming excessively large and potentially exposing more sensitive data over time.
- Store logs securely. Use secure storage mechanisms for logs, similar to how you store secrets.
Advanced Security Considerations: Securing Flask Api With Jwt
Securing a Flask API goes beyond basic authentication. Robust security requires careful consideration of diverse attack vectors and potential vulnerabilities specific to API endpoints. This section delves into advanced strategies for rate limiting, token blacklisting, and mitigating common API attacks, all crucial for a production-ready API.Implementing these advanced techniques ensures your API remains resilient against malicious actors and maintains performance under load.
Securing Flask APIs with JWTs is crucial for protecting sensitive data. Just like San Diego zoos are diligently safeguarding their animal populations, especially given the recent bird flu outbreak impacting flocks worldwide, bird flu has decimated flocks but not at san diego zoos heres how they keep condors penguins and more safe , robust security measures like JWTs are vital for preventing unauthorized access.
This ensures your API remains secure and trustworthy, just like the zoos’ careful animal management protocols.
By carefully designing your security model, you can safeguard sensitive data and maintain a reliable service for legitimate users.
Endpoint-Specific Security
Different API endpoints often have varying levels of sensitivity. A GET request for public data requires less protection than a POST request modifying user accounts. Implementing granular security policies based on the endpoint’s function is essential. This involves tailoring authentication and authorization rules, potentially allowing only specific users or roles to access certain endpoints. For instance, an endpoint responsible for updating user profiles should require more stringent authentication compared to an endpoint for retrieving public resources.
Rate Limiting
Rate limiting is a crucial defensive measure against denial-of-service (DoS) attacks and abusive usage patterns. It restricts the number of requests a user or IP address can make within a specific timeframe.
- This technique prevents abuse and protects your API from overload. Rate limits are typically implemented at the application level or using a dedicated rate limiting library.
- A well-designed rate-limiting system should consider factors like user behavior, request frequency, and IP address patterns to dynamically adjust limits as needed. This flexibility allows you to adapt to varying user loads and maintain service responsiveness.
- Implementing rate limiting often involves setting up thresholds and time windows. For example, a rate limit of 10 requests per minute per IP address would prevent an attacker from flooding the API with numerous requests.
Token Blacklisting
Token blacklisting is a method for revoking access tokens that have been compromised or otherwise invalidated. This prevents unauthorized access even after a token has been issued.
- This approach ensures that compromised tokens cannot be used for malicious activities. Storing revoked tokens in a database or a dedicated blacklisting service is a common practice.
- When a token is flagged as revoked, subsequent requests using that token are rejected. This adds another layer of security, preventing reuse of compromised tokens. The implementation must ensure that the blacklisting process is efficient and doesn’t introduce bottlenecks.
- A robust token blacklisting system should employ a mechanism to check the token’s validity against a list of revoked tokens during authentication. For example, if a token is marked as revoked, the authentication process will return an error.
Protecting Against Common Attacks
Implementing security measures against common attacks is critical for API resilience. These attacks include Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and SQL injection.
- Input validation is a key defense mechanism against XSS and SQL injection vulnerabilities. Sanitizing user inputs prevents malicious scripts or SQL commands from being executed. This involves carefully filtering and escaping potentially harmful characters.
- Employing CSRF protection mechanisms prevents attackers from making unauthorized requests on behalf of legitimate users. Techniques like using anti-CSRF tokens embedded in forms are effective.
Robust Security Model
A robust security model encompasses multiple layers of protection. It combines secure authentication, authorization, rate limiting, and appropriate error handling.
- The model should be designed to address potential vulnerabilities proactively. This includes utilizing a layered approach with various defense mechanisms, such as input validation, secure coding practices, and regular security audits.
- For example, implementing a two-factor authentication system can significantly enhance security, requiring both a password and a one-time code for access.
- Regular security audits are essential for identifying and patching vulnerabilities. Employing security best practices during the API design and development phases can also reduce the risk of potential attacks.
Example API with Complete Implementation
Now that we’ve covered the theoretical underpinnings of securing a Flask API with JWT, let’s delve into a practical example. This complete implementation demonstrates how to combine Flask, Flask-JWT-Extended, and proper authorization to create a secure API. We’ll walk through the code structure, highlighting each component and its role in the authentication and authorization process.
Code Structure and Components
The example API comprises several key components. The core structure includes routes for user registration, login, and protected resources. Crucially, we’ll utilize decorators to enforce authentication and authorization on specific endpoints. This layered approach ensures that only authorized users can access sensitive data.
User Registration and Login Routes
The registration and login routes are responsible for handling user account creation and authentication. A crucial aspect of these routes is validating user input and securely storing passwords using appropriate hashing algorithms. This prevents common security vulnerabilities.
from flask import Flask, request, jsonify
from flask_jwt_extended import create_access_token, jwt_required, get_jwt_identity
import bcrypt
# ... (Import other necessary modules)
app = Flask(__name__)
app.config['SECRET_KEY'] = 'your_secret_key' # Replace with a strong key
# ... (Define user model and database connection)
@app.route('/register', methods=['POST'])
def register():
# ... (Handle user registration logic, including input validation)
# ... (Hash password securely using bcrypt)
# ... (Create user in database)
access_token = create_access_token(identity=user_id)
return jsonify('access_token': access_token), 201
@app.route('/login', methods=['POST'])
def login():
# ... (Handle user login logic, including authentication)
# ... (Compare hashed password)
access_token = create_access_token(identity=user_id)
return jsonify('access_token': access_token), 200
Protected Resources
Protected resources are endpoints that require authentication and authorization. Using the `jwt_required` decorator ensures that only authenticated users can access these endpoints. Further authorization logic can be added based on user roles or other criteria.
@app.route('/protected', methods=['GET'])
@jwt_required()
def protected():
current_user = get_jwt_identity()
# ... (Retrieve data for the authenticated user)
return jsonify('message': 'Protected resource accessed', 'user_id': current_user), 200
Error Handling and Response Management
Robust error handling is critical for a production-ready API. This example demonstrates returning appropriate HTTP status codes and informative error messages for various scenarios, such as invalid credentials or missing tokens. This ensures a smooth user experience.
# ... (Example of handling exceptions and returning appropriate status codes and messages)
try:
# ... (API logic)
except Exception as e:
return jsonify('error': str(e)), 500
Final Thoughts
In conclusion, securing your Flask API with JWTs is a crucial step in ensuring data integrity and user authentication. This guide has walked you through the process of implementing JWT authentication, authorization, error handling, and best practices. By understanding these fundamental principles and following the provided examples, you can build a secure and reliable API that protects your application and user data.
Remember that ongoing security vigilance and staying updated with the latest security practices are vital for maintaining a robust API.