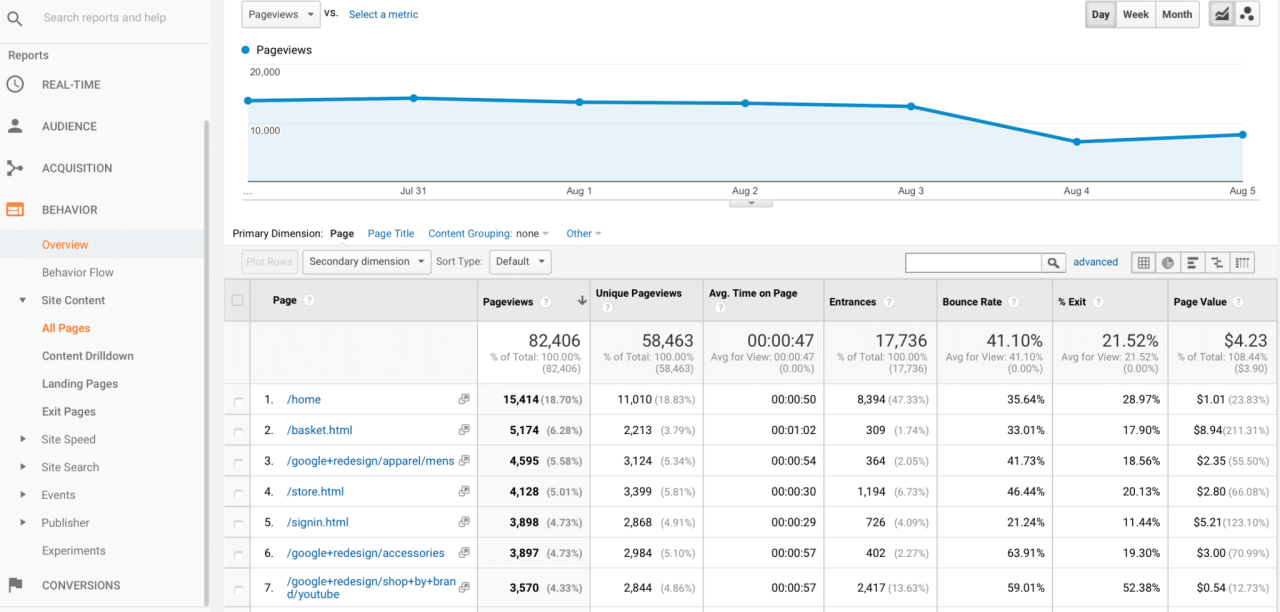
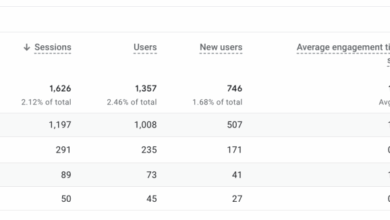
Content marketing metrics to track are crucial for understanding the effectiveness of your content strategy. This guide delves into key metrics, from engagement and reach to conversions, providing actionable insights to optimize your content and achieve your business objectives. We’ll explore how to measure these metrics, analyze trends, and ultimately use data to inform your content strategy for better results.
By understanding and tracking these metrics, you can fine-tune your content creation process, ensure it aligns with your overall business goals, and maximize its impact. This comprehensive guide covers everything from defining the metrics themselves to analyzing performance over time, helping you make data-driven decisions for a successful content marketing strategy.
Defining Content Marketing Metrics
Content marketing isn’t just about creating engaging blog posts; it’s about measuring its impact on business goals. Understanding which metrics to track and how to interpret them is crucial for demonstrating ROI and optimizing future strategies. This in-depth look at content marketing metrics will help you understand their significance and how to use them to achieve your business objectives.Effective content marketing relies heavily on measurable results.
Tracking the right metrics allows you to understand what resonates with your audience, refine your approach, and ultimately, drive business growth. This is achieved through a systematic evaluation of various aspects of your content performance.
Tracking content marketing metrics is crucial for success, and recent headlines like the NYC mayor corruption case dismissed ( nyc mayor corruption case dismissed ) highlight the importance of transparency. Engagement rates, website traffic, and lead generation are just a few key metrics to consider. Analyzing these numbers helps refine strategies and ensure content aligns with target audiences.
Ultimately, effective content marketing hinges on a deep understanding of what’s working and what needs improvement.
Content Marketing Metric Categories
Understanding content marketing metrics is easier when categorizing them. Different categories, like engagement, reach, and conversions, provide a holistic view of content performance. This structure allows for focused analysis and targeted improvement.
- Engagement Metrics: These metrics focus on how actively your audience interacts with your content. High engagement suggests that your content is relevant and valuable to your target audience. Engagement metrics provide valuable insights into the effectiveness of your content strategy and indicate areas for improvement.
- Reach Metrics: These metrics quantify the number of people who have seen or interacted with your content. A wide reach signifies a successful distribution strategy and a broader audience awareness of your brand or product.
- Conversion Metrics: Conversion metrics track the actions users take after engaging with your content. These actions could include signing up for a newsletter, making a purchase, or requesting a demo. Strong conversion rates indicate that your content is effectively driving desired outcomes.
Content Marketing Metrics: A Comprehensive List
This list details various content marketing metrics, categorized for clarity and comprehension. Each metric contributes to a comprehensive understanding of your content’s performance and helps in aligning your efforts with business objectives.
- Website Traffic: This measures the total number of visitors to your website. High traffic suggests that your content is attracting the right audience.
- Page Views: The number of individual pages viewed on your website. High page views can indicate that your content is engaging enough to keep users exploring.
- Time on Page: The average time spent by visitors on a specific page. Longer time on page suggests that your content is valuable and compelling.
- Bounce Rate: The percentage of visitors who leave your website after viewing only one page. A low bounce rate suggests high engagement.
- Social Shares: The number of times your content is shared on social media platforms. High social shares indicate that your content is resonating with your audience and is worthy of spreading.
- Click-Through Rate (CTR): The percentage of people who click on a link in your content. A high CTR suggests that your calls to action are effective.
- Lead Generation: The number of leads generated through your content, such as newsletter sign-ups or contact form submissions. Higher lead generation correlates with more opportunities for sales.
- Conversion Rate: The percentage of visitors who complete a desired action, such as making a purchase or downloading a resource. High conversion rates show effective content strategy.
- Customer Acquisition Cost (CAC): The cost associated with acquiring a new customer. This metric shows the efficiency of your content marketing efforts in generating new customers.
Comparing and Contrasting Content Marketing Metrics
This table provides a structured overview of various content marketing metrics.
| Metric | Description | Formula/Calculation | Importance |
|---|---|---|---|
| Website Traffic | Total number of visitors to a website | Total number of visits | Indicates overall reach and interest in content |
| Page Views | Number of individual pages viewed | Total page views | Shows content depth and engagement |
| Time on Page | Average time spent on a page | Total time spent / Total page views | Indicates content quality and user interest |
| Bounce Rate | Percentage of visitors leaving after one page | (Number of single-page visits / Total visits) – 100 | Indicates content relevance and user experience |
Measuring Engagement Metrics
Content marketing isn’t just about creating great content; it’s about how that content resonates with your audience. Measuring engagement metrics provides crucial insights into how well your content performs and helps you understand what resonates with your target audience. This allows for strategic adjustments and improvements to future content creation.Understanding audience engagement is vital for tailoring content strategies.
By analyzing how people interact with your content, you gain a deeper understanding of their preferences and needs. This understanding leads to more effective content creation, improved conversion rates, and stronger brand loyalty.
Social Media Engagement Metrics
Social media platforms are powerful tools for content engagement. Tracking key metrics allows you to understand how your content is performing in this space.
- Likes, Comments, and Shares: These are fundamental metrics. Likes indicate basic interest, comments demonstrate deeper engagement, and shares amplify your reach. Tracking these numbers provides insights into content appeal.
- Reach and Impressions: Reach shows the number of unique users who saw your content, while impressions track the total number of times your content was displayed. These metrics help you gauge the potential visibility of your content.
- Click-Through Rates (CTRs): The percentage of users who clicked on a link in your social media post is a key metric. High CTRs indicate strong interest and compelling content.
- Engagement Rate: This metric represents the overall level of interaction with your content. A higher engagement rate generally suggests more successful content.
To measure social media engagement, use the built-in analytics tools of each platform. Tools like Facebook Insights, Twitter Analytics, and Instagram Insights provide detailed data on likes, shares, comments, reach, and more. This data is crucial for understanding audience response and optimizing future content.
Blog Post Engagement Metrics
Blog posts offer a different set of engagement metrics to monitor. Analyzing these metrics reveals how your blog content resonates with readers.
- Time on Page: This metric reflects how long readers spend on your blog posts. Longer time on page suggests the content is engaging and relevant.
- Bounce Rate: The percentage of visitors who leave your site after viewing only one page (like your blog post) is the bounce rate. A lower bounce rate signifies that your content is keeping readers engaged.
- Page Views: Tracking the number of page views provides a measure of the overall visibility of your blog post.
- Comments and Shares: Comments show reader interaction and provide valuable feedback. Shares demonstrate the content’s potential to be disseminated and spread within the reader’s network.
Using analytics platforms like Google Analytics, you can easily track these blog post metrics. This data gives you a comprehensive understanding of how your blog content performs.
The Importance of User Comments and Shares
User comments and shares are crucial indicators of content performance. They represent genuine engagement and validation of your content.
Comments provide valuable feedback, allowing you to understand your audience’s perspective. Shares extend your content’s reach, introducing it to a broader audience.
Comments and shares are invaluable for understanding what your audience finds interesting and valuable. They also offer insights into potential areas for improvement in future content creation. They’re essential for content optimization.
Engagement Metrics Table
The table below summarizes key engagement metrics and their impact.
| Metric | Description | Example Measurement | Impact |
|---|---|---|---|
| Likes on Facebook Post | Number of likes received on a Facebook post. | 150 likes on a post about a new product. | Indicates initial interest in the product. |
| Comments on a Blog Post | Number of comments left by readers on a blog post. | 10 insightful comments on a post about a new product. | Shows engagement and provides feedback on the post’s quality. |
| Shares on Twitter | Number of times a Twitter post is shared. | 25 shares of a post about a company event. | Amplifies reach and exposes the content to a wider audience. |
| Time on Page (Blog Post) | Average time spent by visitors on a blog post. | Average time on a blog post is 3 minutes. | Indicates the post is engaging and relevant. |
Tracking Reach and Visibility Metrics

Understanding how far your content reaches and how visible it is is crucial for evaluating its effectiveness. This involves more than just counting views; it’s about assessing the impact your content has on your audience and its overall influence. Analyzing reach and visibility allows you to optimize your content strategy and maximize its potential.Measuring content reach and visibility goes beyond basic impressions.
It requires looking at where your content is appearing, how it’s being shared, and the overall impact it has on your brand and audience. This is a critical aspect of content marketing, as it directly relates to the effectiveness of your efforts.
Methods to Measure Content Reach
Different methods exist to track the reach of your content. Knowing where your audience interacts with your content is vital for understanding its impact. Social media shares, backlinks, and website traffic are all valuable indicators of content reach.
- Website Traffic Analysis: Tools like Google Analytics provide valuable insights into website traffic. This includes metrics like unique visitors, page views, bounce rate, and time on page. These metrics help determine how many people are engaging with your content directly. For instance, a high bounce rate from a specific blog post might indicate a problem with the content’s quality or relevance to the user.
- Social Media Engagement: Social media platforms offer built-in analytics to track reach and engagement. Metrics like likes, shares, comments, and retweets offer insight into how your content resonates with your audience on these platforms. For example, a post that consistently generates high engagement rates likely appeals to your target audience and could be a good model for future content.
- Backlink Analysis: The number and quality of backlinks pointing to your content are a significant indicator of its authority and reach. Tools like Ahrefs or SEMrush can help identify and analyze backlinks. A high number of backlinks from reputable sources signifies a higher level of credibility and reach.
Metrics to Evaluate Content Visibility
Evaluating content visibility goes beyond just counting views. It involves understanding where your content appears in search results, its visibility on social media, and its overall presence online.
- Search Engine Ranking: Monitoring your content’s position in search engine results pages (SERPs) is crucial. Tools like SEMrush can track your rankings. High rankings indicate strong visibility and improved chances of reaching a larger audience. For example, ranking highly for relevant s on Google can drive substantial organic traffic to your website.
- Social Media Reach: The number of people who see your content on social media platforms is a key visibility metric. Social media analytics tools offer insights into the reach of your posts. For example, a high reach on Twitter for a specific tweet might mean that your message resonated with a large portion of your followers.
- Domain Authority: Your website’s authority is a significant factor in visibility. Tools like Moz offer metrics related to domain authority. A higher domain authority signifies greater trust and credibility, which can lead to increased visibility in search results.
Tools for Tracking Website Traffic
Several tools can assist in tracking website traffic related to content performance. Choosing the right tool depends on your specific needs and budget.
- Google Analytics: A free and powerful tool for analyzing website traffic, providing comprehensive data on user behavior, including page views, bounce rate, and time on page. This is often a cornerstone of website traffic analysis.
- SEMrush: A robust tool that provides insights into rankings, backlink analysis, and website traffic. It’s a valuable tool for content marketers seeking in-depth analysis.
- Ahrefs: Another powerful tool that offers similar features to SEMrush, including backlink analysis, research, and website traffic data. It is a valuable asset for content marketers aiming to optimize their online presence.
Measuring Content Influence on Social Media
Measuring content influence on social media platforms is essential to understand its impact on your audience. Analyzing engagement metrics, shares, and reach helps evaluate its overall effectiveness.
- Social Media Analytics: Each social media platform offers built-in analytics. Facebook Insights, Twitter Analytics, and Instagram Insights provide data on reach, engagement, and impressions. This data is invaluable in determining how well your content resonates with your audience on each platform.
- Social Listening Tools: Tools like Brand24 or Hootsuite allow monitoring conversations and mentions related to your content. This gives insight into how your content is being discussed and perceived by your audience.
Reach Metrics Table
| Metric | Description | Measurement Method | Significance |
|---|---|---|---|
| Unique Visitors | Number of distinct users visiting a webpage | Google Analytics, website traffic tools | Indicates the breadth of your content’s reach |
| Page Views | Total number of times a page is viewed | Google Analytics, website traffic tools | Reflects the frequency of content consumption |
| Social Media Shares | Number of times content is shared on social media platforms | Social media analytics | Indicates virality and audience engagement |
| Backlinks | Number of links from other websites to your content | Backlink analysis tools | Indicates authority and credibility of your content |
Analyzing Conversion Metrics
Content marketing isn’t just about creating engaging content; it’s about driving tangible results. Understanding how your content translates into conversions is crucial for measuring its effectiveness and optimizing your strategy. This involves a deep dive into the metrics that reveal how your content influences the customer journey, ultimately leading to sales and increased revenue.Conversion metrics go beyond simple website visits and engagement; they provide a clear picture of the impact your content has on achieving specific business goals.
Tracking website traffic and engagement is key in content marketing, but sometimes, tragic news like the recent shooting in West Oakland, man fatally shot in west oakland 14 , can dramatically shift priorities. While that’s important to cover, remembering to monitor click-through rates and conversion rates remains vital for any successful content strategy. Analyzing these metrics ensures your content is truly hitting the mark and engaging your audience.
By meticulously tracking these metrics, you gain valuable insights into what resonates with your audience and what content strategies yield the best results. This allows you to fine-tune your approach and maximize the return on your content marketing investment.
Key Conversion Metrics Related to Content Marketing
Content marketing aims to drive specific actions from your audience. These actions, from signing up for a newsletter to purchasing a product, are measured through various conversion metrics. Identifying and tracking these metrics is vital for understanding the success of your content strategy.
- Lead Generation Rate: This metric measures the effectiveness of your content in generating potential customers. A high lead generation rate indicates your content is attracting the right audience and engaging them sufficiently to take the next step. For example, a blog post about a new product feature could include a call-to-action (CTA) encouraging readers to download a whitepaper or sign up for a webinar, thereby generating leads.
- Conversion Rate: This measures the percentage of visitors who complete a desired action. A higher conversion rate suggests that your content is convincing visitors to take the desired action. For instance, if a landing page features a clear call-to-action for a free trial, a high conversion rate signifies that the page is effective in persuading visitors to try the product.
- Customer Acquisition Cost (CAC): CAC represents the total cost of acquiring a new customer. A lower CAC indicates that your content marketing efforts are cost-effective in bringing in new customers. For example, running a targeted social media campaign or sponsoring a relevant webinar to generate leads can be compared to the cost of other acquisition channels to determine which is more effective.
Measuring Lead Generation from Content
Lead generation is a cornerstone of content marketing success. Tracking these leads allows you to understand what content resonates most with your target audience and to refine your strategy accordingly.
- Tracking Forms and CTAs: Integrate tracking codes with your website’s forms and CTAs to monitor how many people are filling out forms or clicking on specific calls-to-action. This allows you to identify which content pieces are driving the most leads.
- Lead Scoring and Segmentation: Assign scores to leads based on their engagement and activity. Segment your leads based on their characteristics and interests. This allows for more targeted follow-up and communication.
- Attribution Modeling: Use attribution modeling to determine which pieces of content contributed most to lead generation. This provides valuable insights into your content’s effectiveness and allows for better allocation of resources.
Tracking Sales Generated from Content
Linking content to sales requires meticulous tracking. Identifying the content that drives the most conversions is critical for optimizing your content marketing strategy.
- Sales Attribution: Utilize sales attribution tools to determine which content influenced a customer’s decision to make a purchase. This provides a detailed view of the customer journey and the content that had the biggest impact.
- Sales Funnels: Analyze the sales funnel to understand where customers drop off. Content plays a crucial role in each stage of the funnel. For instance, educational blog posts can nurture leads, while targeted landing pages can drive conversions.
- Sales Revenue by Content Type: Track sales revenue generated from different types of content (e.g., blog posts, videos, infographics). This allows you to assess the effectiveness of different content formats and adjust your content strategy accordingly.
Content Influence on Customer Journeys and Conversions
Content acts as a catalyst in guiding customers through their purchase journeys. Its influence on conversions is significant.
| Metric | Description | Calculation/Measurement | Impact |
|---|---|---|---|
| Lead Generation Rate | Percentage of website visitors who become leads. | (Number of leads generated / Number of website visitors) – 100 | Higher rate indicates better content attracting potential customers. |
| Conversion Rate | Percentage of leads who convert into customers. | (Number of customers / Number of leads) – 100 | Higher rate indicates content effectively persuades leads to purchase. |
| Customer Acquisition Cost (CAC) | Total cost of acquiring a new customer. | Total marketing costs / Number of new customers | Lower CAC signifies more efficient content marketing efforts. |
Analyzing Content Performance Over Time
Tracking content performance isn’t a one-time snapshot; it’s a continuous journey. Understanding how your content performs over time provides invaluable insights into audience engagement, content effectiveness, and overall marketing strategy optimization. Analyzing trends and patterns reveals which content resonates best and helps you tailor future content creation to maximize impact.Analyzing content performance over time requires more than just looking at immediate results.
It demands a strategic approach that considers the context, the evolution of your audience, and the changing landscape of your industry. This allows you to make data-driven decisions and refine your content strategy for consistent growth and success.
Methods for Tracking Content Performance Over Time
Regular monitoring of key metrics is crucial for understanding long-term content trends. Establish a consistent schedule for data collection, ensuring you’re using the same metrics and tools across all periods. This consistency is vital for accurate comparisons and reliable trend analysis. Tools like Google Analytics, social media analytics dashboards, and custom reporting systems can automate the process and save significant time.
Comparing the Performance of Different Content Types
To effectively compare different content types, you need to establish consistent measurement criteria for each. This involves defining specific, measurable, achievable, relevant, and time-bound (SMART) goals for each content type. For example, you might track unique page views for blog posts, engagement metrics for social media posts, and download counts for downloadable resources. Categorizing content into specific types (e.g., blog posts, infographics, videos) will allow you to analyze performance trends within each category.
This will reveal which content formats resonate most strongly with your audience.
Analyzing Trends in Content Marketing Metrics
Identifying trends in your metrics is crucial for future content planning. Observe patterns in engagement, reach, and conversions over time. For example, if you notice a consistent increase in social media shares for a particular blog post series, you can adapt your future content strategy to focus on topics that generate similar levels of engagement. A careful examination of these trends will reveal valuable insights into audience preferences and content that resonates with them.
Tracking content marketing metrics is crucial for success. Engagement metrics like website traffic and social media shares are essential, but you also need to consider how easily your audience finds answers. A robust knowledge base, like the ones available from best knowledge base software , can significantly impact user experience and ultimately, your content marketing ROI. Focusing on user satisfaction through well-organized FAQs and readily available information is a key content marketing metric to watch closely.
Use visualizations to make trends easily identifiable.
Using Graphs and Charts for Visualizing Content Performance, Content marketing metrics to track
Visual representations of your data are crucial for quick comprehension and pattern identification. Line graphs are excellent for tracking metrics over time. Bar charts can effectively compare the performance of different content types. Scatter plots can display correlations between variables. These tools will provide a clear and concise overview of your content performance, allowing you to quickly identify key trends and make data-driven decisions.
Example Table of Content Performance Tracking
| Date | Content Type | Metric | Value |
|---|---|---|---|
| 2024-08-15 | Blog Post | Unique Page Views | 1,500 |
| 2024-08-15 | Social Media Post | Engagement Rate | 5% |
| 2024-08-16 | Blog Post | Unique Page Views | 1,700 |
| 2024-08-16 | Social Media Post | Engagement Rate | 6% |
| 2024-08-17 | E-book | Downloads | 100 |
Choosing the Right Metrics for Your Goals
Content marketing success hinges on understanding your goals and selecting the right metrics to track progress. Simply collecting data isn’t enough; meaningful insights emerge when metrics are carefully chosen to align with your specific business objectives. This involves more than just vanity metrics; it’s about identifying the indicators that truly reflect the impact of your content on key business outcomes.Effective content marketing is a strategic process.
Choosing the correct metrics allows you to evaluate the effectiveness of your strategies and optimize your approach for maximum impact. This process ensures that your efforts are not just producing content, but are actually driving the desired results.
Selecting Appropriate Content Marketing Metrics
To ensure your content marketing efforts align with business objectives, you must meticulously select the metrics that will reflect the true impact. This requires a deep understanding of your specific goals. A well-defined metric will track the key aspects of your success and pinpoint areas needing improvement.
- Consider the desired outcomes. Are you aiming to increase brand awareness, generate leads, or boost sales? Clearly defining your objectives will guide the choice of relevant metrics.
- Analyze your target audience. Understanding their behavior and preferences helps identify the metrics that best reflect their engagement with your content. What are the key interactions you want to measure? Are they downloading resources, visiting specific pages, or engaging with social media posts?
- Evaluate your existing data. Review your current analytics to identify which metrics already provide valuable insights. This allows you to build upon existing knowledge and avoid unnecessary complexities.
Aligning Metrics with Business Objectives
Effective content marketing metrics must directly correlate with your business goals. Choosing the wrong metrics can lead to wasted effort and a misinterpretation of results.
- If your primary goal is lead generation, metrics like landing page visits, form submissions, and lead conversion rates should be prioritized.
- For boosting brand awareness, focus on metrics like social media engagement, website traffic, and brand mentions.
- If your aim is to drive sales, track metrics like conversion rates, revenue generated from content-driven campaigns, and customer acquisition costs.
Prioritizing Metrics Based on Importance
Not all metrics are created equal. Prioritize those that directly contribute to your most critical business objectives. A well-structured prioritization strategy allows for efficient resource allocation and effective measurement.
- Identify the key performance indicators (KPIs) that directly impact your business goals.
- Evaluate the impact of each metric on your bottom line.
- Rank the metrics according to their significance, allocating more attention and resources to the most crucial ones.
Examples of Different Content Marketing Goals and Relevant Metrics
This table showcases different content marketing goals and the corresponding relevant metrics.
| Goal | Relevant Metrics | Description |
|---|---|---|
| Increase Brand Awareness | Social Media Engagement, Website Traffic, Brand Mentions | Track the reach and engagement with your brand across various platforms. |
| Generate Leads | Landing Page Visits, Form Submissions, Lead Conversion Rates | Measure the effectiveness of your lead magnets and landing pages. |
| Drive Sales | Conversion Rates, Revenue Generated from Content-Driven Campaigns, Customer Acquisition Cost | Analyze the revenue impact of your content marketing initiatives. |
| Improve Customer Retention | Customer Lifetime Value, Customer Churn Rate, Repeat Purchases | Assess the value and longevity of your customer relationships. |
Final Review: Content Marketing Metrics To Track
In conclusion, tracking content marketing metrics is essential for success. By meticulously monitoring engagement, reach, conversions, and performance over time, you gain a deeper understanding of what resonates with your audience. This data-driven approach allows for continuous improvement, ensuring your content consistently delivers results and aligns with your business objectives. This guide provides the framework for effectively tracking these vital metrics and ultimately maximizing the return on your content investment.