Enable CORS HTTPOnly cookie secure token is crucial for secure web applications. It ensures that your site can interact safely with other domains while protecting sensitive data like cookies and tokens. This guide will delve into the intricacies of CORS, HTTPOnly cookies, secure tokens, and their integration for a robust and secure web experience.
This comprehensive guide will explain how to implement CORS to enable requests from different origins to access your cookies. We’ll discuss the security implications of bypassing HTTPOnly cookies through CORS, and how secure tokens can be used to authorize requests from different origins. We’ll also cover troubleshooting common CORS issues, highlighting potential vulnerabilities and how to mitigate them.
Understanding CORS (Cross-Origin Resource Sharing)
CORS, or Cross-Origin Resource Sharing, is a mechanism that allows a web browser to securely request resources from a different domain than the one the browser is currently on. This is crucial for applications that need to interact with external APIs or services hosted on different servers. Without CORS, a browser would often block such requests due to security concerns, potentially hindering functionality.CORS works by establishing a communication protocol between the requesting origin (the website making the request) and the resource origin (the server hosting the resource).
The resource origin defines the rules for which origins are permitted to access its resources. This controlled access ensures that only authorized requests are processed, protecting against malicious attacks.
CORS Request Methods
CORS supports various HTTP request methods, each with a specific purpose. Understanding these methods is vital for designing effective cross-origin interactions. Common methods include GET, POST, OPTIONS, PUT, and DELETE. Each method dictates how the request will interact with the resource. For example, GET requests are typically used to retrieve data, while POST requests are often used to send data to the server for processing.
OPTIONS requests are used to determine the available methods for a given resource.
- GET: This method is used to retrieve data from a resource. It’s often used for fetching data from an API endpoint.
- POST: This method is used to send data to a server for processing, such as submitting a form or creating a new resource.
- OPTIONS: This method is used to determine the available HTTP methods and headers for a given resource. It’s crucial for preflight requests, which are a key part of the CORS mechanism.
- PUT: This method is used to update a resource on the server. It replaces the existing resource with the new data.
- DELETE: This method is used to delete a resource on the server.
CORS Headers
CORS headers are crucial for enabling cross-origin requests. They define the rules and permissions for the resource origin to communicate with other origins. These headers are sent as part of the response from the server to the client. A critical part of this process is the preflight request.
- Access-Control-Allow-Origin: This header specifies the origins that are allowed to access the resource. A value of “*” allows all origins, while a specific domain (e.g., “https://example.com”) permits only that origin.
- Access-Control-Allow-Methods: This header specifies the HTTP methods that are allowed for cross-origin requests. A value of “GET, POST” would allow only GET and POST requests.
- Access-Control-Allow-Headers: This header specifies the headers that are allowed in cross-origin requests. This is vital for requests that include custom headers. A value of “Content-Type” would allow requests with a Content-Type header.
- Access-Control-Expose-Headers: This header specifies the headers that should be exposed to the requesting origin. This is important for controlling which headers the client can access from the response.
- Access-Control-Max-Age: This header sets a time-to-live value for the preflight response. This reduces the number of preflight requests required, improving performance.
Examples of CORS Headers and Impact
Consider a scenario where a frontend application (origin A) needs to access data from a backend API (origin B). The backend server (origin B) needs to set appropriate CORS headers in its response. For example, the backend might set:“`Access-Control-Allow-Origin: https://originA.comAccess-Control-Allow-Methods: GET, POST, OPTIONSAccess-Control-Allow-Headers: Content-Type“`These headers tell the frontend application that requests from origin A are allowed, using GET, POST, or OPTIONS methods, and that the `Content-Type` header is allowed in the request.
CORS Headers Table
| Header | Description |
|---|---|
| Access-Control-Allow-Origin | Specifies origins allowed to access the resource. |
| Access-Control-Allow-Methods | Specifies allowed HTTP methods (e.g., GET, POST). |
| Access-Control-Allow-Headers | Specifies allowed request headers. |
| Access-Control-Expose-Headers | Specifies headers to be exposed in the response. |
| Access-Control-Max-Age | Sets time-to-live for preflight responses. |
Implementing CORS for HTTP Only Cookies
HTTP Only cookies are a crucial security measure to prevent client-side JavaScript from accessing cookie values. This prevents malicious scripts from stealing sensitive information, like session tokens or authentication data. However, if your application needs to allow requests from different origins to access resources, including cookies, implementing CORS correctly is paramount. This involves careful configuration to permit specific origins while ensuring the security of HTTP Only cookies.CORS, by design, doesn’t inherently allow access to HTTP Only cookies.
Enabling CORS, HTTPOnly, cookie secure tokens is crucial for robust security, especially when dealing with sensitive data like photo backups. Thinking about self hosted photo backup alternatives? A strong security setup, including properly configured cookies, is paramount to protect your precious memories from unauthorized access. Implementing these measures ensures the integrity of your data, whether you’re using a cloud service or a self hosted photo backup alternatives solution.
Ultimately, a secure setup is key to preventing breaches and keeping your photos safe.
The browser’s security model prevents JavaScript from directly accessing these cookies. The CORS mechanism only dictates whether or not the browser allows the request to proceed, not whether it allows JavaScript to access the data. Therefore, proper server-side configuration is critical to correctly handling HTTP Only cookies within a CORS context.
Configuring the Server for CORS and HTTP Only Cookies
CORS is primarily controlled by the server. The server must respond to preflight requests with appropriate headers. These headers dictate the origins that are allowed to access the resource, including whether cookies should be sent. This involves meticulously configuring the server to send the correct CORS headers. The `Access-Control-Allow-Origin` header is essential, specifying the origins that are allowed to access the resource.
Crucially, this header needs to be carefully configured to align with the security requirements.
Protecting HTTP Only Cookies from Client-Side JavaScript
HTTP Only cookies are designed to prevent client-side JavaScript from accessing their values. This protection is inherent in the browser’s security model. Even if CORS allows access from a different origin, the browser will not expose the cookie’s value to JavaScript. This fundamental protection ensures that malicious scripts cannot extract sensitive information.
Security Implications of Bypassing HTTP Only Cookies through CORS
While CORS itself does not bypass the HTTP Only protection, improper implementation or configuration of CORS can inadvertently create security vulnerabilities. A poorly configured CORS setup, allowing requests from unintended origins or using overly permissive policies, can expose resources and data that should remain protected. Therefore, it’s essential to configure CORS headers meticulously and carefully consider the security implications of allowing access from different origins.
Securely Sharing Data Between Origins Using Cookies
While HTTP Only cookies cannot be directly accessed by client-side JavaScript, there are secure methods for sharing data between different origins. One approach involves using a token-based authentication system. These tokens are exchanged between the origins and stored securely, eliminating the need to directly access cookies. Another method involves using a server-side proxy to handle requests and responses from different origins.
The proxy can manage access and authentication, further enhancing security. This approach is useful when dealing with sensitive information or complex authorization requirements.
Enabling CORS, HTTPOnly cookies, and secure tokens is crucial for web security, especially when dealing with sensitive data. This is particularly important when you’re building a robust API. Thinking about real-world applications, a recent example is the sale of a single family residence for 1.5 million in San Ramon 2-2. single family residence sells for 1 5 million in san ramon 2 2 The security measures surrounding such transactions, especially the financial aspects, highlight the importance of these security protocols.
So, ensuring proper CORS, HTTPOnly cookies, and secure tokens is paramount for a secure and trustworthy online experience, even for property sales.
Secure Tokens and CORS
Secure tokens are crucial for web applications, ensuring that only authorized users can access sensitive data and perform specific actions. They act as digital passports, verifying the identity and permissions of the user interacting with the application. Implementing robust token management is paramount for protecting user data and preventing unauthorized access.Protecting tokens from unauthorized access is a primary concern when dealing with CORS requests.
CORS allows resources from different origins to interact, but this introduces a potential security vulnerability if tokens aren’t handled carefully. A well-designed token system, combined with appropriate CORS configurations, significantly enhances the overall security posture of a web application.
Importance of Secure Tokens
Secure tokens are essential for authentication and authorization. They verify the identity of a user, granting access to specific resources or functionalities based on their permissions. This prevents unauthorized access and maintains data integrity. Without secure tokens, applications become vulnerable to various attacks, potentially leading to data breaches and compromised accounts.
Token Generation, Storage, and Validation
Generating secure tokens involves creating unique, cryptographically strong identifiers that represent user credentials. These tokens typically contain information about the user, their permissions, and an expiry time. Storing tokens securely is equally critical. Database encryption, secure storage mechanisms, and secure session management are all important aspects to consider. Token validation involves verifying the authenticity and validity of the token.
This typically involves checking the token’s signature, expiry date, and other relevant attributes to ensure its legitimacy. The validation process needs to be robust and efficient to protect against malicious attacks.
Secure Token Usage with CORS Requests
To ensure secure token usage with CORS requests, the server must properly handle token validation. The token should be sent in the request header, usually in a custom header, for CORS requests. The server can then validate the token and allow or deny access based on the validation result. The client-side application should ensure that the token is sent securely with the CORS request.
This might involve using HTTPS and secure transmission protocols. For instance, if the token is sent in the Authorization header, the browser will automatically use HTTPS to transmit the token to the server.
Token Validation Methods and Security Strengths
| Validation Method | Security Strengths | Weaknesses |
|---|---|---|
| HMAC-based signature validation | Strong authentication, suitable for protecting sensitive data, computationally efficient. | Vulnerable to attacks if the secret key is compromised. |
| JSON Web Token (JWT) validation | Compact, self-contained, often used for authorization, includes claims, digital signatures. | Reliance on a robust signature algorithm and key management is crucial. |
| OAuth 2.0 tokens | Standardized, robust, authorization framework, well-established security practices. | Complexity in implementation, requires careful consideration of scopes and permissions. |
Different validation methods offer varying degrees of security. HMAC-based validation is computationally efficient but vulnerable to key compromises. JWTs are compact and include claims, but rely on robust signature algorithms. OAuth 2.0 tokens are standardized and offer robust authorization, but require careful implementation. Choosing the right validation method depends on the specific security needs of the application.
HTTP-Only Cookies and Secure Tokens
Integrating HTTP-only cookies and secure tokens into a CORS-enabled application is crucial for robust security. This approach significantly mitigates the risk of client-side script accessing sensitive data and manipulating cookies. Secure tokens, when combined with proper cookie attributes, provide an additional layer of protection against cross-site scripting (XSS) attacks and man-in-the-middle (MITM) exploits.This section delves into the best practices for integrating these security measures, highlighting how to use secure tokens for authorization and how to protect the tokens themselves.
We’ll also explore techniques to minimize vulnerabilities and mitigate risks when dealing with cross-origin requests.
Best Practices for Integration
Proper implementation of HTTP-only cookies and secure tokens requires careful attention to detail. Setting the `HttpOnly` flag prevents client-side JavaScript from accessing the cookie, significantly reducing the attack surface. Secure tokens, in addition to being generated with robust cryptographic methods, should be used for all authentication and authorization logic.
Using Secure Tokens for Authorization, Enable cors httponly cookie secure token
Secure tokens serve as a crucial component in authorizing requests from different origins. They act as credentials, verifying the user’s identity and their permissions. These tokens, typically generated on the server-side, are often digitally signed or hashed to ensure their integrity. By verifying the token’s signature or hash on each request, the server can authenticate the user without exposing sensitive data.
Securing the Token Itself
Protecting the token from unauthorized access is paramount. This includes using strong cryptographic algorithms for token generation and storage. Tokens should be stored securely on the server, ideally using encryption. Tokens should also be designed with an expiration time to prevent prolonged access. Regularly rotating tokens and implementing appropriate access control mechanisms on the server side further enhances security.
Avoiding Vulnerabilities
Several methods can help to prevent vulnerabilities when integrating HTTP-only cookies and secure tokens with CORS. Employing a secure communication channel (HTTPS) is essential. Verifying the origin of the request is a critical step. The server should always validate the origin against a predefined whitelist to prevent malicious requests from unauthorized domains.
Mitigating Risks with Tokens and Cookies
Risks associated with using tokens and cookies in cross-origin requests are minimized by following stringent security guidelines. Strict input validation on the server side can prevent attacks like cross-site request forgery (CSRF). The token itself should be designed with a short lifetime, encouraging frequent token renewal and minimizing the potential impact of a compromised token. Restricting access to specific resources based on the token’s claims can further limit the potential damage from a breach.
Example Implementation (Conceptual)
Imagine a scenario where a user logs in to a website. The server generates a secure token and sets an HTTP-only cookie with this token. Subsequent requests from the client include this token, which the server verifies. The server, upon successful verification, grants access to the requested resources. This example illustrates the importance of the token for authorization in a CORS-enabled environment.
Enabling CORS (Cross-Origin Resource Sharing), HTTPOnly cookies, and secure tokens is crucial for API security. This is particularly important when dealing with sensitive data, like those in online services. Given the recent shift in strategy by abortion opponents, focusing on restricting access to abortion pills, abortion opponents shift focus to pills , it’s even more critical to have robust security measures in place for online services to prevent unauthorized access and data breaches.
Strong security measures, including CORS, HTTPOnly cookies, and secure tokens, remain essential to protect sensitive data and maintain user trust in online services.
Security Considerations for CORS, Cookies, and Tokens
Implementing Cross-Origin Resource Sharing (CORS), HTTP-only cookies, and secure tokens enhances the security posture of web applications. However, these security measures are not foolproof and require careful consideration of potential vulnerabilities. Understanding these risks and their mitigation strategies is crucial for building robust and trustworthy online experiences.Proper configuration and implementation of these technologies are paramount to prevent unauthorized access and data breaches.
Failure to address potential security gaps can lead to significant consequences, ranging from data leaks to compromised user accounts. This discussion delves into the security considerations, outlining potential attack vectors and mitigation strategies.
Potential Security Risks
The combination of CORS, HTTP-only cookies, and secure tokens, while providing a strong foundation, is not impenetrable. Careless implementation can create avenues for malicious actors to exploit. For instance, if the CORS configuration is improperly defined, attackers might gain unauthorized access to resources. Similarly, weak token generation or inadequate cookie management practices can expose sensitive information.
Common Attack Vectors
Several attack vectors can target applications utilizing CORS, cookies, and tokens. A common approach is Cross-Site Scripting (XSS) attacks. By injecting malicious scripts into a vulnerable application, attackers can potentially steal tokens or cookies, gaining unauthorized access. Another potential vulnerability is CSRF (Cross-Site Request Forgery). Attackers might manipulate a user’s session to perform unwanted actions.
Mitigation Strategies
Several robust mitigation strategies can minimize the risks Artikeld above. For example, rigorous input validation is critical to prevent XSS attacks. Furthermore, employing strong token generation algorithms and secure storage mechanisms will protect sensitive information. Implementing robust security policies to handle CORS requests and validating requests against CORS configuration rules can mitigate potential risks.
HTTPS’s Role in Security
HTTPS plays a crucial role in securing interactions involving CORS, cookies, and tokens. HTTPS encrypts communication between the client and server, preventing eavesdropping and tampering. This encryption protects the confidentiality of data transmitted, including sensitive information like tokens and cookies. Moreover, HTTPS establishes a secure channel, bolstering the integrity of the connection.
Vulnerability Analysis and Mitigation
| Vulnerability Type | Description | Mitigation Strategy ||—|—|—|| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into a web application. | Input validation, output encoding, and Content Security Policy (CSP). || Cross-Site Request Forgery (CSRF) | Attackers manipulate a user’s session to perform unwanted actions. | CSRF tokens, double submit cookie, and same-site cookies. || CORS Misconfiguration | Improper CORS configuration allows unauthorized access to resources.
| Strict CORS policies, careful review of CORS configuration, and comprehensive testing. || Weak Token Generation | Tokens are vulnerable to cracking or prediction. | Strong token generation algorithms, frequent token rotation, and secure storage. || Cookie Handling Vulnerabilities | Improper handling of cookies can lead to data breaches. | HTTP-only cookies, secure flag for cookies, and proper cookie expiration mechanisms.
|
Real-World Examples and Use Cases: Enable Cors Httponly Cookie Secure Token
CORS, HTTP-only cookies, and secure tokens are crucial for building secure and robust web applications. These technologies work together to prevent cross-site scripting (XSS) attacks, protect sensitive data, and allow legitimate cross-origin interactions. Understanding their practical applications in different contexts is vital for effective implementation.These technologies are fundamental to creating secure APIs and user interfaces. By restricting access to resources and protecting user data, developers can significantly enhance the overall security posture of their applications.
The specific implementation and configuration will vary depending on the application’s needs and the nature of the data being exchanged.
E-commerce Platforms
E-commerce sites often use APIs to allow third-party payment gateways to process transactions securely. This integration requires CORS to enable communication between the e-commerce platform and the payment gateway. HTTP-only cookies are used to manage user sessions and prevent unauthorized access to sensitive data like payment details. Secure tokens, often JWTs (JSON Web Tokens), are used to authenticate users and authorize access to specific resources.
The combination allows secure transactions and ensures that payment information is handled properly and safely.
Social Media Applications
Social media applications leverage APIs for user authentication, data retrieval, and sharing. CORS allows external applications to interact with the social media platform, for example, an app that lets users share content from the platform. HTTP-only cookies and secure tokens protect user accounts and ensure data integrity. This allows developers to securely integrate functionalities that enhance the user experience.
For example, integrating with external services that facilitate sharing on social media.
Mobile Banking Applications
Mobile banking applications often need to interact with third-party services or APIs for functionalities such as payment processing, account information retrieval, and notifications. CORS enables secure communication with these services. HTTP-only cookies and secure tokens are critical to protect sensitive financial data. This combination prevents unauthorized access and ensures the security of transactions.
Use Cases and Security Considerations
| Use Case | Security Considerations |
|---|---|
| E-commerce platforms | Protecting payment information, preventing unauthorized access to transaction data, ensuring secure communication with payment gateways. |
| Social Media Applications | Protecting user accounts, preventing unauthorized access to user data, ensuring the integrity of shared content. |
| Mobile Banking Applications | Protecting financial data, preventing unauthorized access to account information, securing transactions. |
| Single Sign-On (SSO) Platforms | Protecting user credentials, ensuring secure authentication across multiple applications, preventing unauthorized access to resources. |
Tailoring Solutions to Different Needs
The specific implementation of CORS, HTTP-only cookies, and secure tokens will vary depending on the application’s needs. For example, an application that only needs to communicate with a single, trusted third-party API might require a simpler CORS configuration than an application that interacts with multiple, potentially untrusted services.The level of security required will also vary. Applications handling sensitive financial data will need stronger security measures than applications handling less sensitive information.
Careful consideration of the specific needs of the application and the potential risks associated with the data being handled is essential.
Troubleshooting CORS Issues
CORS (Cross-Origin Resource Sharing) is a crucial aspect of web security, but sometimes, issues arise. Troubleshooting these problems often requires a methodical approach, understanding the configuration, and applying effective debugging techniques. This section delves into strategies for identifying and resolving common CORS problems, particularly those related to cookies and tokens.Debugging CORS errors involves understanding the communication between the client (e.g., a web browser) and the server.
Incorrect configurations or misinterpretations of the CORS headers can lead to unexpected behavior and errors. Careful examination of the request and response headers is paramount in pinpointing the source of the problem.
Common CORS Errors and Resolutions
Incorrect CORS headers on the server side are a frequent source of issues. A server might not be properly configured to allow requests from specific origins, or the headers might be missing or incomplete. This can manifest in various ways, from requests being blocked to the inability to send cookies or tokens. Understanding the expected headers and their values is vital for accurate troubleshooting.
- Missing or Incorrect Access-Control-Allow-Origin Header: The server needs to explicitly state which origins are allowed to access its resources. If this header is missing or incorrect, the browser will often reject the request. Correcting this involves ensuring the header is present and includes the correct origin. For example, if the client is from ‘https://example.com’, the server must include ‘https://example.com’ in the Access-Control-Allow-Origin header.
If the server should accept requests from multiple origins, a wildcard ‘*’ can be used, though it is less secure.
- Incorrect Access-Control-Allow-Methods Header: The server needs to specify the HTTP methods (e.g., GET, POST, PUT) allowed for requests from specific origins. Incorrect or missing values here can prevent the client from performing necessary actions. Ensuring the correct HTTP methods are included is crucial.
- Missing Access-Control-Allow-Headers Header: The server must declare which headers are allowed in the request. This is crucial for requests carrying custom headers, like those used for authentication. The header must explicitly list headers like Authorization, X-Custom-Header, etc. A missing or incorrect header can prevent successful requests.
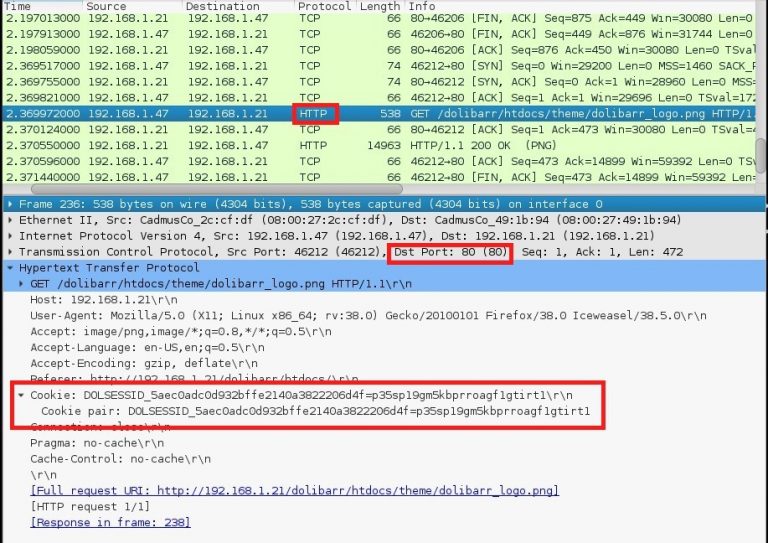
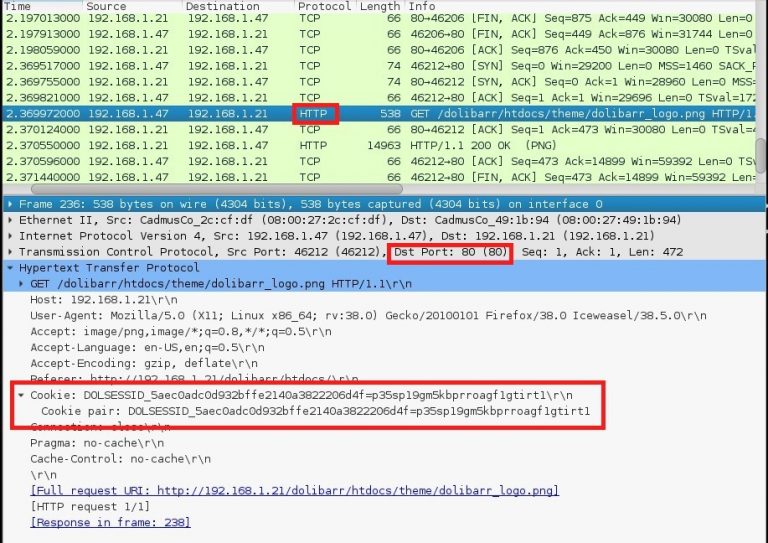
- Cookie issues (HTTPOnly and Secure flags): If cookies aren’t properly configured on the server, the client might not be able to send them to the server for authentication. Checking the HTTPOnly and Secure attributes of cookies is essential. These attributes ensure that cookies cannot be accessed by JavaScript and are transmitted over HTTPS, respectively. If these attributes are not correctly set, the browser may not send the cookie as expected.
- Token-related errors: If tokens are not correctly handled, authentication can fail. The server might not be configured to accept tokens or validate them correctly. The CORS configuration needs to account for the token being sent in the header or as part of the request body. Ensure the server is properly validating the tokens and providing the correct CORS headers in response.
Debugging CORS-related Problems
Effective debugging involves careful inspection of the network requests and responses. Tools like browser developer tools provide invaluable insights into the headers exchanged between the client and server. Examining the request and response headers allows for identification of missing or incorrect CORS headers. Using a tool like Postman or similar API testing tools can aid in crafting specific requests and inspecting the responses in greater detail.
These tools will show the headers and allow for more accurate debugging.
Table of Common CORS Errors and Resolutions
| Error | Resolution |
|---|---|
| Missing `Access-Control-Allow-Origin` header | Add the correct `Access-Control-Allow-Origin` header to the server response, specifying the allowed origin(s). |
| Incorrect `Access-Control-Allow-Methods` header | Ensure the `Access-Control-Allow-Methods` header includes the permitted HTTP methods (e.g., GET, POST, PUT). |
| Missing `Access-Control-Allow-Headers` header | Include the `Access-Control-Allow-Headers` header to specify the allowed request headers, such as `Authorization` or custom headers. |
| Cookie not being sent | Verify the `HTTPOnly` and `Secure` attributes are set correctly on the cookie in the server’s response. |
| Token validation failure | Ensure the server is correctly validating the token and responding with appropriate CORS headers. |
End of Discussion
In conclusion, implementing CORS, HTTPOnly cookies, and secure tokens is essential for building secure and robust web applications. By understanding the principles and best practices discussed here, you can safeguard your application against common vulnerabilities and create a more secure online experience for your users. Remember to always prioritize security and regularly update your configurations to stay ahead of evolving threats.